DETECT AND CLOSE SECURITY LACKS Vulnerability- management
Fast, proactive and around the clock. Establish vulnerability management that goes beyond CVE scans and patch management to close security gaps before they become problems.
Enginsight is the all-in-one cybersecurity platform from Germany that analyzes your security posture, detects threats and prevents attacks automatically – as SaaS and on-premises.












Automated vulnerability scan Identify and close vulnerabilities
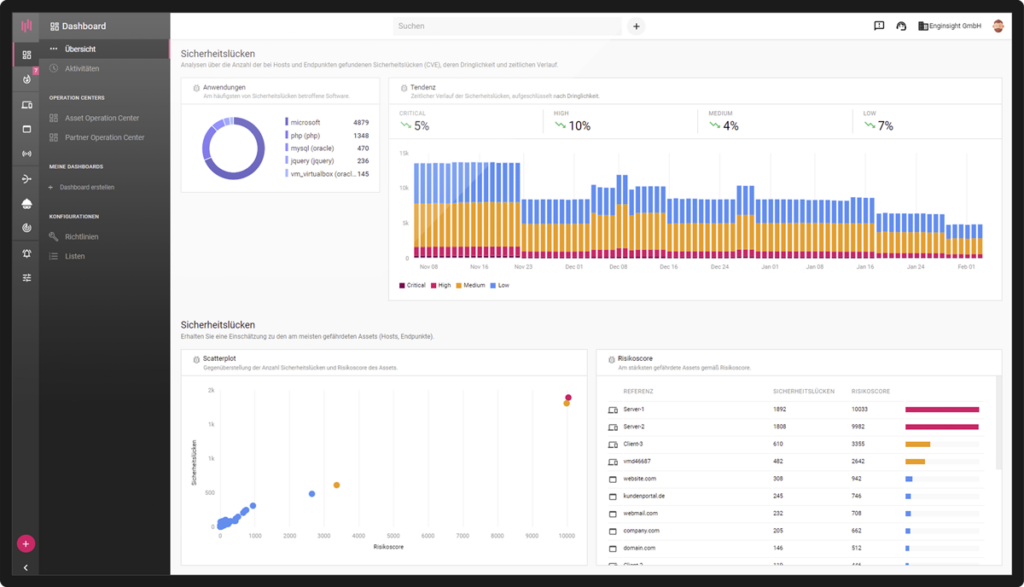
What vulnerabilities (CVEs) specifically exist in my IT infrastructure? With Enginsight’s vulnerability scanner, you can see the affected assets and patch them immediately. The severity rating helps with prioritization. In this way, you always maintain an overview of the security status of your IT.
Everything in view with the vulnerability management tool
Correct prioritization thanks to the view of the entire IT
Bring the vulnerabilities of your entire IT environment into one view. This way, you are always informed about the security status of all assets and know where the most urgent action is needed.
- Inform responsible persons
- Clear dashboard
- Risk assessment of each asset
- BSI risk assessment of your vulnerabilities
Whitebox analyses with CVE scan
Highest quality of data
Thanks to the agent installed directly on your servers and clients, you get valid vulnerability assessments. With continuous monitoring for vulnerabilities, you are immediately informed about a changed security situation.
- Validation of the security vulnerabilities
- Permanent vulnerability monitoring
- Alert on new security gaps
Proactively uncover vulnerabilities
Eliminate hazards
Respond adequately to threats at all times, apply patches directly from the platform or automate your update processes. Beyond the basics, Enginsight gives you configuration management and the attacker’s view.
- Import and automate updates
- Manage configurations
- Automated pentest
- Vulnerabilities from three perspectives for the entire IT
Play Pentest Video
SOFTWARE FOR EFFECTIVE VULNERABILITY MANAGEMENT
The more you know about your own IT landscape, the more secure you can make your systems sustainable. Our vulnerability management tool is an important cornerstone here. However, IT security involves more than just CVE scans and patch management.


Function overview in detail Technical details on vulnerability management
Would you like to know a little more? Then you are exactly right here! Find out what Enginsight does for you in detail when it comes to vulnerability management in a completely automated way.
The Pulsar Agent installed on servers and clients enables detection and inventory of all installed software. The operating system libraries are examined as well as the files on the hard disk are scanned with the extended software monitoring in order to include non-regularly installed software in the inventory (e.g. portable apps, programs embedded in other applications, Java libraries).
The software inventory forms the best data basis for the actual vulnerability scan, the comparison of the installed software with known security vulnerabilities (Common Vulnerabilities and Exposures, or CVE for short). Thanks to the installation of the agent, valid results are guaranteed and false positives are minimized.
- Platform independent (Windows & Linux)
- Best database thanks to software inventory
- Valid results
- Minimization of false positives
Enginsight can also be used to scan network peripherals on which a Pulsar Agent cannot be installed for security vulnerabilities. Websites can also be monitored for vulnerabilities. For this purpose, a sensor is placed in the network (Hacktor) or Internet (Observer). Subsequently, entire networks can be scanned for vulnerabilities.
From the outside, the sensors examine the open ports and the web application for vulnerable software. By optionally storing access data (auth provider), operating systems and installed software can be retrieved, results expanded and validation improved.
- Scan networks for security vulnerabilities
- Websites and web portals
- Deposit auth providers for SNMP, WMI, SSH
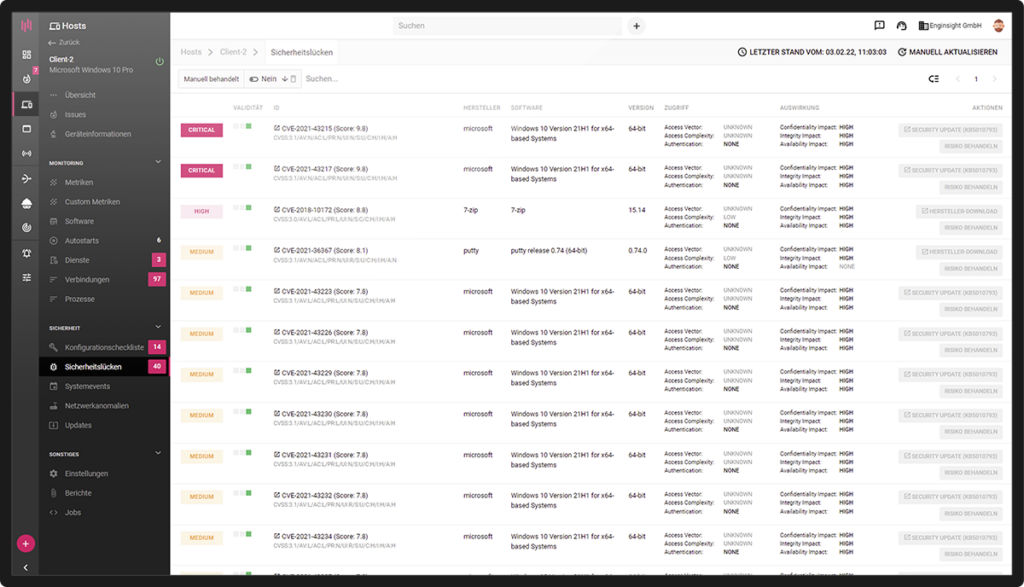
The associated CVE identifier is given for all security vulnerabilities. The CVS score (Common Vulnerability Scoring System: 1 to 10) enables categorization according to urgency. With a risk score for each asset, users can prioritize patch management by threat. An alarm immediately informs responsible persons about new security vulnerabilities.
Further information on each vulnerability in the NIST database and additional sources on the Internet are linked, for example on possible exploits.
- CVS-Scoring (CVSS)
- Risk score
- Urgency level
- Integration with alarm system
- Linking of further information
Each CVE detected by Enginsight is validated via the available meta-information and including the software type. It then receives an assessment via the validity traffic light, which guarantees full transparency.
Most of the information for validation is available to the vulnerability scan via the Pulsar Agent, so there is always a high level of validity. All assets on which a Pulsar Agent can be installed should therefore be equipped with the software component.
- Validation based on meta information
- Validity traffic light
- Valid results for CVE scan with Pulsar agent
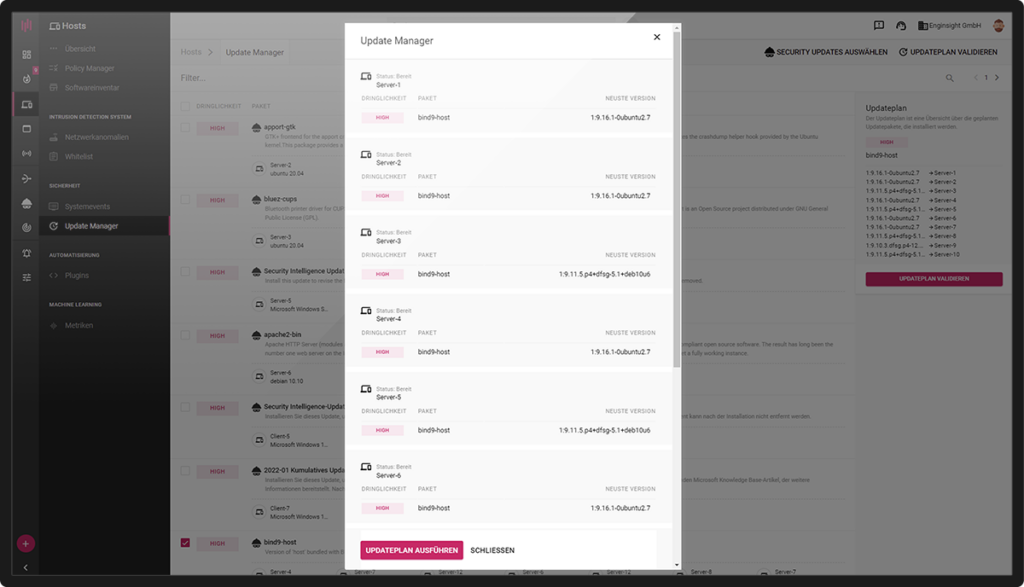
To bring vulnerable software to a safe state, an update to the current version is usually sufficient. Enginsight’s Update Manager enables the targeted import of updates across multiple servers and clients. In addition, updates can be fully automated, and automatic updates can also be limited to security-related updates. The tag system allows convenient configuration even in large IT environments.
- Platform independent (Linux & Windows)
- Compatible with Windows Server Update Services (WSUS)
- Patching third-party Software on Linux systems
Next to insecure software, faulty configurations represent a second category of risk that you can effectively address with Enginsight’s configuration management.
Use autofixes to correct configurations directly from the Enginsight platform.
The Security Technical Implementation Guides (STIGs) integrated for all common operating systems can be extended with your own guidelines. This also allows documentation requirements to be fulfilled effectively.
- Microsoft Windows 10
- Microsoft Server 2008/2012/2016/2021
- Canonical Ubuntu 16/18/20
- Red Hat Enterprise 6
- SUSE Linux Enterprise 12

Vulnerability Management FAQ
Vulnerability management is important for companies and organizations to protect their IT systems and infrastructure against cyber threats and data loss. This involves identifying, assessing and closing known and potential vulnerabilities in IT systems before they can be exploited by attackers.
Effective vulnerability management includes the following steps:
- Vulnerability detection (vulnerability scanner)
- Risk assessment / risk management
- Vulnerability Elimination
- IT monitoring / supervision
A vulnerability scanner is an automated IT security tool that detects vulnerabilities in IT systems. It scans the network for known security vulnerabilities (CVEs) and provides an overview of the potential risks that can arise from these gaps.
More information: Perform comprehensive CVE scans from three perspectives
Vulnerability Management System (VMS) is a framework that aims to perform vulnerability management in an organized and systematic manner. A VMS includes security tools, processes and procedures necessary for monitoring, identifying, assessing and closing vulnerabilities in IT systems and networks.
Enginsight vulnerability scanning is part of the Enginsight Cybersecurity Platform.
Would you like to know how you can improve your IT security with Enginsight? We would be happy to analyze your current status and real needs in the area of IT and network security together with you.