File Integrity Monitoring Integrity monitoring of critical files
File Integrity Monitoring (FIM) is a building block of a comprehensive IT security strategy. It involves monitoring system-critical files or folders to detect unauthorized changes.
With Enginsight, you can detect these automatically and intervene proactively. Find out why this is important for compliance requirements here.
INTEGRITY & CONSISTENCY
Keeping an eye on system configurations
Data breaches – whether caused by cyberattacks, system failures or human error – can have a significant impact. They can lead to loss of critical data, disruption of business processes, and reputational damage.
How do you ensure that the integrity of your data and systems is maintained? Traditional security tools often don’t capture all changes or are too complex to manage efficiently. Effective file integrity monitoring is therefore a challenge for many organizations.
DETECT UNUSUAL BEHAVIOR
Ransomware indicator
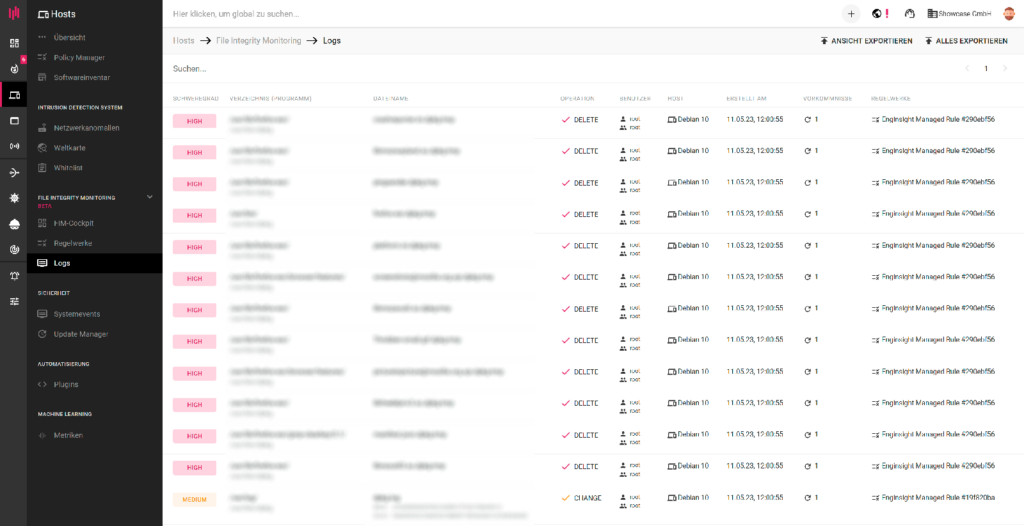
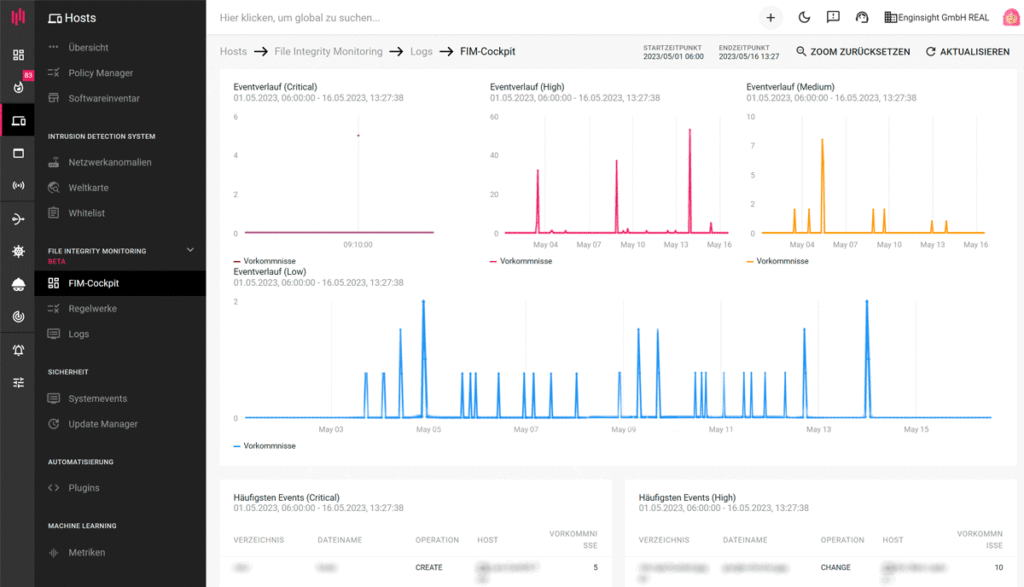
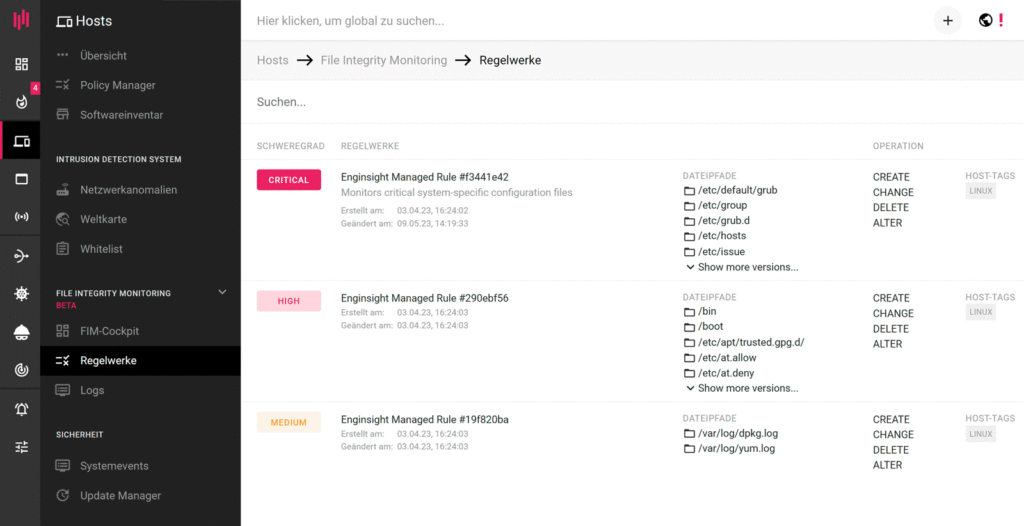
A company’s critical files are the focus of attackers. In the case of ransomware attacks, FIM serves as an important early detection tool. By assigning different criticality levels to certain files and directories, unusual or clustered activities can be detected particularly quickly.
Continuous monitoring also detects unauthorized changes. Enginsight alerts notify the responsible administrators of an urgent need for action.
FIM-Video abspielen
Enginsight is the all-in-one cybersecurity platform from Germany that analyzes your security posture, detects threats and prevents attacks automatically – as SaaS and on-premises.












FIM is the guardian & detective for your data The main advantages of File Integrity Monitoring
- Detect unauthorized changes
- Protection against data manipulation
- Adhere to compliance requirements
- Early detection of vulnerabilities
- System integrity recovery
- Ransomware protection
- Basis for forensic investigations
LOGGING OF ACCESSES
Error analysis even easier
In the event of system crashes or other failures, a look at the FIM file monitoring helps. The collection of changes made enables administrators to search specifically for adjustments in a given period and check potential sources of errors. Misconfigurations are thus uncovered and the performance of the IT infrastructure is improved.
PROACTIVE DEFENSE
Detect unauthorized changes
SECURITY GUIDELINES
Meet compliance requirements
Monitor and log changes to files to more easily comply with security policies. FIM logs help you ensure that your IT systems comply with regulatory requirements.
They also provide auditors with solid evidence of system and file integrity during an audit.

FAQ about File Integrity Monitoring
FIM is a technology that tests operating system (OS), database and application files and checks for tampering or corruption. File integrity monitoring is an IT security process that succeeds through a FIM.
The integrity of a file is determined by means of checksums. A comparison is made with a known, trusted version to verify validity.
Who made changes and what specifically was changed? These are two other important attributes that FIM records.
FIM includes monitoring of changes to files and system settings. SIEM analyzes event data to detect activities that indicate security threats, such as failed login attempts and privilege escalation.
Enginsight’s File Integrity Monitoring is part of the Enginsight Cybersecurity Platform.
Would you like to know how you can improve your IT security with Enginsight? We would be happy to analyze your current status and real needs in the area of IT and network security together with you.