 Guideline for KRITIS operators
Guideline for KRITIS operators
Cybersecurity for critical infrastructure
The IT Security Act 2.0 calls for numerous changes and requirements for CRITIS operators and companies in the special public interest. Particular emphasis is placed on the use of attack detection systems in accordance with Section 8a (1a) BSIG. This will be mandatory as of May 01, 2023.
Find out here how to implement the BSI recommendations simply and sustainably.









BSI recommendations simply implement
Cyber attacks are (unfortunately) part of everyday IT life today. The question is no longer if, but when an attack will occur. The attack scenarios are diverse and constantly present IT managers with new challenges. Because one thing is clear: attacks must be (automatically) defended against; the consequences of a successful cyberattack could be fatal, especially if critical infrastructures are affected.
What is the “BSI Orientation Guide”?
The BSI Guidance is a comprehensive document from the BSI. It outlines mandatory requirements for the use of attack detection systems (SzA) and divides these into three phases: LOGGING, DETECTION, and RESPONSE. The measures described therein are divided into SHOULD, MUST, and CAN requirements, and are also prioritized into three levels, depending on the desired “maturity level.”
In the first step, achieving maturity level 3 is sufficient. Operators of critical infrastructures should aim for level 4 in the long term. Therefore, there is a continuous improvement of IT security measures, which is absolutely sensible and necessary given the aspect of the constantly increasing and more complex threat landscape.
What is KRITIS?
KRITIS (critical infrastructures) are all organisations and institutions that are of enormous importance to the state community. This includes, for example, the healthcare system, medical care, but also the energy and water supply. A failure or disruption of these social functions can have considerable consequences for public safety.
BSI-KRITIS-Regulation (BSI-KritisV) and German IT Security Act 2.0 (IT-SiG 2.0) therefore require “appropriate organizational and technical precautions”. From May 2023, operators of critical infrastructures will be obliged to use systems for attack detection, among other things. Which systems are suitable for this purpose remains an open question. It is not uncommon for those affected to be unsure which systems are really suitable and needed. SIEM systems are the first systems that come to mind. But, contrary to what many expect, they are not without alternative!
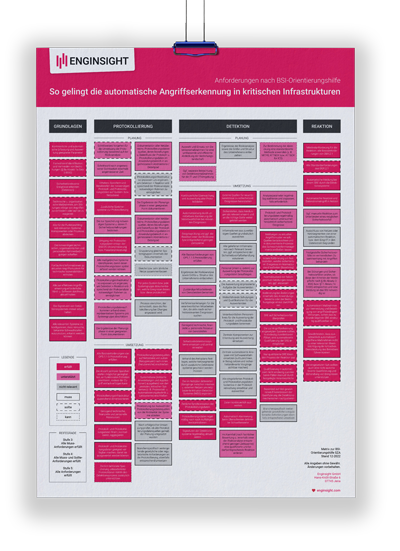
Enginsight Matrix for BSI Guidance
Find out at a glance how Enginsight supports you in implementing the BSI Guidance according to § 8a Paragraph 3 BSIG.
Automated systems for attack detection and defense
When it comes to securing your IT infrastructure and complying with the legal requirements for critical infrastructures, we support you from planning to implementation. In this way, you achieve at least maturity level 3, demonstrate cyber resilience and secure your “Digital Compliance”.
Below is a small excerpt of which requirements from the “BSI orientation guide for the use of attack detection systems” you can fulfill with Enginsight and the appropriate service providers. The Enginsight matrix for the BSI orientation guide provides you with a complete overview.
KRITIS audit - how the KRITIS verification is carried out
All companies that belong to the KRITIS operators are obliged to have a special audit report drawn up in order to prove to the Federal Office for Information Security (BSI) that their IT security measures correspond to the current state of the art. This requires a KRITIS audit to be carried out by an external auditor in accordance with Section 8a (3) BSIG. After a successful audit, the security of your IT infrastructure is confirmed by an independent and accredited testing centre.
The exact security requirements vary depending on the industry and are specified in the industry-specific security standards (B3S) recognised by the BSI. These standards specify which measures are required to ensure an optimum level of security.
KRITIS requirements for companies
1. Designation of a contact point
Companies that are considered KRITIS operators are obliged to designate a contact point by setting up a functional mailbox. The aim is to be consistently accessible to the BSI so that IT security information can be sent to the KRITIS operator’s mailbox.
2. Obligation to report IT malfunctions and security incidents
In the event of an unplanned and unusual disruption as well as immediate cyberattacks against your IT infrastructure, KRITIS companies must be reported to the BSI using the functional mailbox.
3. Staying ‘state of the art’
The KRITIS Regulation states that all critical infrastructure companies must implement the latest cyber security protection measures. The international standards and norms such as DIN. ISO, DKE and ISO/IEC. As part of a KRITIS audit, updates on these precautions must also be demonstrably submitted to the BSI every two years.
4. KRITS audit
To ensure that all KRITIS operators meet their obligations for standardised IT security protection, all companies that provide critical services in KRITIS sectors must undergo an audit. The audit takes place every two years and can be verified by a KRITIS audit.
If you need help with the KRITIS requirements and are perhaps unsure whether you have all the IT assets required for the KRITIS audit, please contact us.
- Continuous anomaly detection in real time based on communication data (metadata and content) and log data
- Specifically designed for monitoring and anomaly detection in IT networks, connectable to other systems (e.g. SIEM) via standard interfaces
- Fully automated response processes can be implemented (intrusion prevention / IPS) for direct threat stop
- Comprehensive data collection of communications and network events; in addition, log data is collected on systems and stored in a targeted manner for forensic investigations
- Log data can be anonymized as required (data protection)
- Evaluation of the collected data and classification and alert function
- Autonomous event response and anomaly mitigation, managed services from Enginsight partners provide additional organizational and staffing support
- Host-based IDS detects the specific payload of a possible attack and can block successful execution thanks to IPS; integrated endpoint detection response module protects against malicious code
- Anomaly messages are prioritized by criticality and color-coded; defined alerts, customizable user and group policies
- Comprehensive vulnerability management
- Automated intrusion into the network stream by means of Intrusion Prevention System (IPS)
- In addition to automated qualification, manual handling of vulnerabilities and events is possible
- Running operation remains unaffected while handling suspicious network communication
- For faults with mandatory reporting, the message can be enriched with analysis data from Enginsight
- Enginsight can automatically alert in case of safety-relevant events

Status quo How well are you positioned so far?
If your company is KRITIS-regulated and you are still unsure whether your measures are sufficient: Take an inventory. An analysis of your IT infrastructure creates transparency. Once the deviations between the actual and target state have been determined, you can initiate the necessary measures in a prioritized manner.
With Enginsight, the inventory of your IT assets succeeds at the push of a button.
We will be happy to show you live how quickly this can be done. Contact us.
In the long term and sustainably, Enginsight helps you with the live monitoring of your IT infrastructure. We would be happy to tell you more about this in a live demo or one of our webcasts.
FAQ on KRITIS requirements
The KRITIS regulation in Germany refers to critical infrastructures that are essential for the country. These include:
- Energy: companies that provide electricity and gas.
- Water: companies responsible for drinking water supply and wastewater disposal.
- Information technology and telecommunications: provider of IT and communications services.
- Health: hospitals and other medical facilities.
- Transportation and traffic: this includes both public transportation and major transportation hubs.
According to the BSI, operators of critical infrastructures will have to prove that they meet the KRITIS requirements by May 1, 2023, and every two years thereafter.
Operators of critical infrastructures (KRITIS) in Germany have certain obligations under the BSI Act (BSIG) and the BSI Criticality Ordinance:
- You must designate a point of contact for the Critical Infrastructure you operate.
- You are obliged to report IT malfunctions or significant impairments.
- You must implement “state of the art” IT security.
- You must demonstrate to the BSI every two years that you meet these requirements.
If KRITIS operators do not comply with these requirements on time, they may face sanctions. The exact sanctions or fines are specified in the BSI Act and other legal regulations. It is therefore important that KRITIS operators inform themselves precisely about their obligations and possible consequences in the event of violations.
Some basic requirements are the same for all operators of critical infrastructures and the BSI’s handout, the so-called “BSI Orientation Guide“, is based on these. Other standards apply in addition, but on a sector-specific basis.
The BSI does not specify any concrete technologies to be used. It is undisputed that the use of classic antivirus programs is not sufficient.
The publication “Recommendations for the development and use of products used in critical infrastructures” by UP KRITIS (a public-private cooperation of operators of critical infrastructures, associations and government agencies) is worth reading in connection with the products used.
According to the BSI orientation guide, the results of the audits, tests or certifications carried out on the systems for attack detection, including the security deficiencies uncovered in the process and the maturity level achieved, must be communicated.
The implementation level model is intended to successively increase the quality of systems for attack detection. The maturity level shows whether there is still potential or need for action to optimize IT security or in the use of SzA. The lower the maturity level, the greater the need for action.
The guidance provides operators with a rough framework and thus allows scope for individual implementation. The formulations in the guidance and the implementation levels are based on the BSI’s IT-Grundschutz.


