SIEM system from Enginsight Your SIEMphony for cyber attack detection and defense
Enginsight SIEM (Security Information and Event Management) gives you proactive, real-time protection and comprehensive security intelligence across all data sources. Like a good symphony, all the software components in Enginsight work together and automatically enrich the SIEM system with information from the area of attack detection. This allows you to create not just reactive logging, but proactive security.
Log management and logging The SIEM tool with integrated attack detection system

Enginsight’s all-in-one platform supports the SIEM tool in complying with legal and industry-specific standards. Fulfil the technical cybersecurity requirements for KRITIS and in future also NIS2 – today.

Pseudonymization of personal data within logs. Define responsibilities and individual user roles for depseudonymization. All data can be hosted on your premises as an on-premises solution.

The all-in-one platform helps meet regulatory and industry standards. Meet the technical cybersecurity requirements for KRITIS and future NIS2 – today.
Enginsight combines the most important security functions, such as vulnerability management, intrusion detection, data integrity monitoring or micro-segmentation with the functions of a SIEM system and thus creates not only reactive logs, but proactive IT security for all IT environments.












SIEM Software - COMPREHENSIVE RISK MANAGEMENT for your company
SIEM stands for ‘Security Information and Event Management’. Sounds complicated, but it’s not! The SIEM tool is your personal control centre for more security in the organisation. Like a detective with a magnifying glass and trench coat, a SIEM system monitors all security alarms in real time, keeps an eye on network traffic and keeps a watchful eye on the activities of all users and applications. With the help of a SIEM system, you can sleep easy knowing that your IT security is in the best hands.
LOGMANAGEMENT IN SIEM SYSTEMS Your control center for intelligent safety analyses
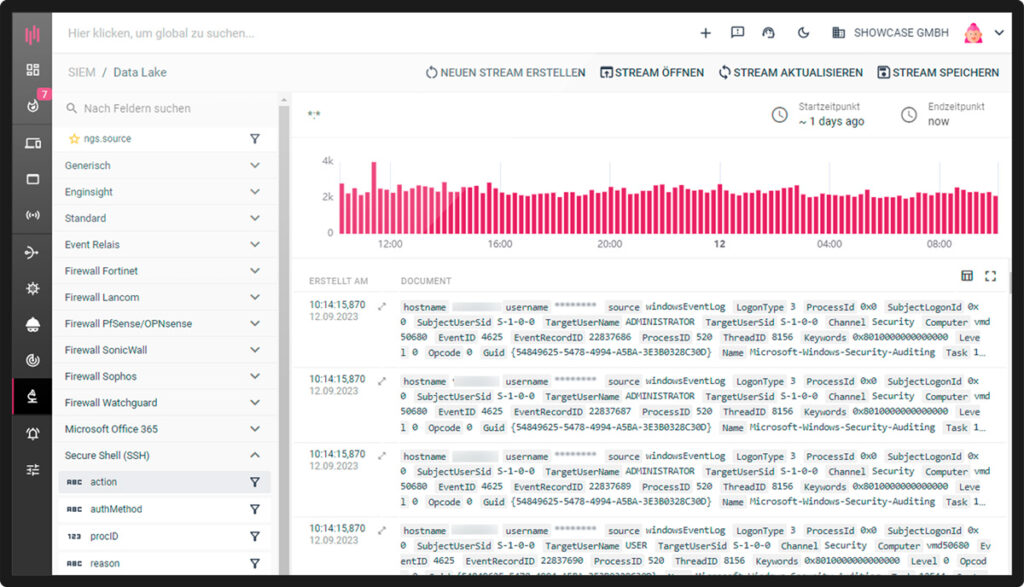
The Datalake acts as a central and adaptable database and thus represents the foundation of the entire SIEM system. It acts as the main repository and combines all the raw data collected.
This data is indexed, grouped and presented in normalized form.
In this way, the Datalake lays the foundation for identifying patterns, irregularities and potential threats.
Thanks to the clever use of the collected data, the SIEM software can efficiently identify security events and perform forensic analyses.
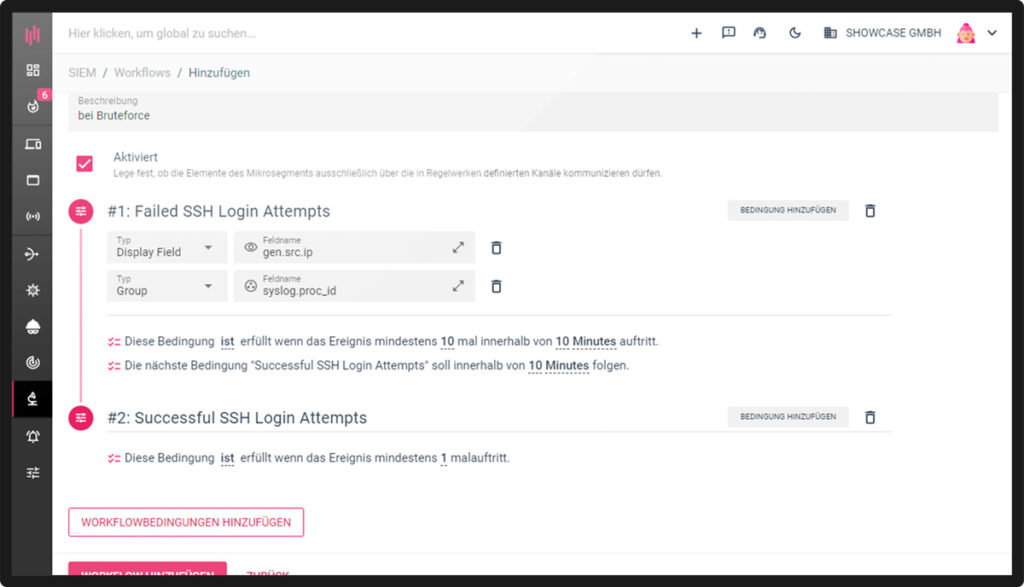
Automate security Customized workflows
By automating responses to specific security events, the SIEM workflows included in the SIEM system can help you reduce the time between detecting and resolving security incidents. With a few simple clicks, you can link different logs and integrate alerts in relation to defined scenarios.
In short, SIEM workflows are an indispensable tool to strengthen your security infrastructure, detect and respond to attacks, and meet compliance requirements.
- Adaptation to specific requirements
- Compliance-Management
- Optimization of resources of your IT team
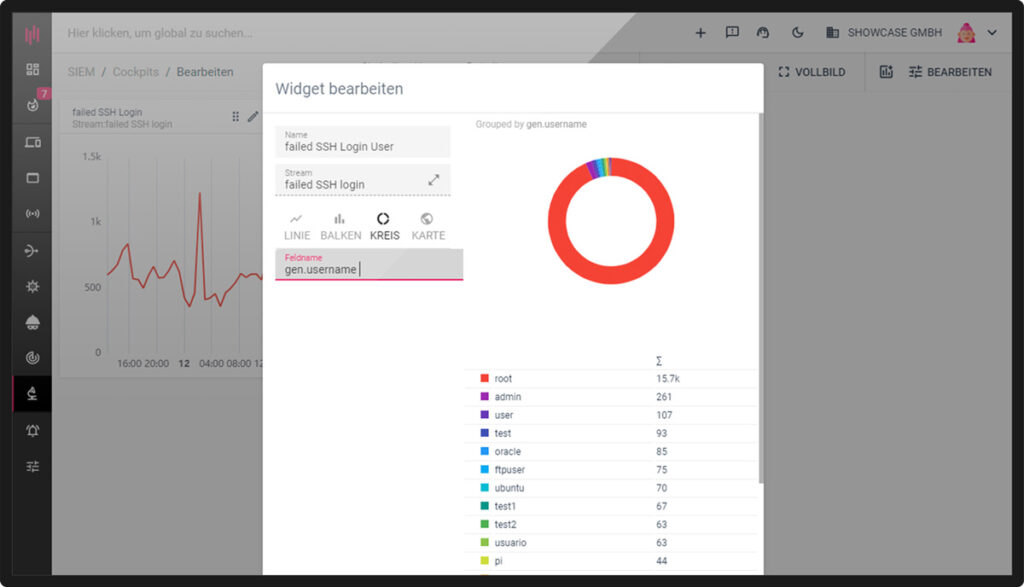
Live overviews Customized dashboards
Who knows the needs of your company better than you? Within the SIEM software in the ‘Cockpits’ area, you can customise your own dashboards. Each display in the cockpit is based on a predefined or customised event stream. You also have the freedom to create different views based on a single stream.
- Darkmode for your Security Operation Center (SOC)
- Individual scaling of the widgets
- Mapping of all data/scenarios from your log
- Multiple dashboards possible for different scenarios
Reference video
IT’S NOT ABOUT IT SECURITY, IT’S ABOUT OPERABILITY AND RESILIENCE
Effective risk management requires continuous condition monitoring in combination with preventive measures as well as a data basis for forensic analyses.
SIEM SOLUTIONS Functions & applications of the SIEM software
Would you like to know more about the SIEM system?
Find out how the Enginsight SIEM tool works and how it makes your daily security work easier.
An electric utility could become the target of a cyberattack aimed at disrupting the power supply. A SIEM system can detect such attacks at an early stage and initiate countermeasures to maintain the power supply.
A telecom provider could be subject to attacks such as DDoS that aim to disrupt service. SIEM solutions can detect these attacks and respond quickly to ensure service availability.
From the outside, the sensors examine the open ports and the web application for vulnerable software. By optionally storing access data (auth provider), operating systems and installed software can be retrieved, results expanded and validation improved.
- Scan networks for security vulnerabilities
- Websites and web portals
- Deposit auth providers for SNMP, WMI, SSH
Airports and train stations rely on complex IT systems. An attack on these systems could paralyze traffic. A SIEM system can identify such attacks and enable rapid response to keep traffic flowing.
Hospitals manage sensitive patient data and rely on medical devices. A cyberattack could compromise this data or affect the devices. SIEM systems can help maintain data integrity and ensure patient safety.
Water utilities could be the target of an attack that compromises water quality. A SIEM solution can help protect the integrity of the water supply by detecting attacks and initiating countermeasures.
Food producers could be impacted by cyberattacks on their production facilities. SIEM systems can detect and remedy production disruptions to ensure food supply.
Use autofixes to correct configurations directly from the Enginsight platform.
The Security Technical Implementation Guides (STIGs) integrated for all common operating systems can be extended with your own guidelines. This also allows documentation requirements to be fulfilled effectively.
- Microsoft Windows 10
- Microsoft Server 2008/2012/2016/2021
- Canonical Ubuntu 16/18/20
- Red Hat Enterprise 6
- SUSE Linux Enterprise 12
Banks and insurance companies are frequent targets of cyberattacks aimed at stealing financial data. SIEM systems can monitor unusual transactions and raise the alert to prevent financial loss.
MAKING THE INVISIBLE VISIBLE - MAKING THE INSECURE SECURE SIEM Industry solutions
In addition to the SIEM tool, you can find more information about your industry requirements and how to fulfil them with Enginsight here.
Your industry is not listed here? Please let us know and we will work out the degree of fulfilment of your standard with the help of Enginsight.
FAQ about the SIEM from Enginsight
The SIEM software is an add-on to your existing Enginsight licence and is available from just € 2.20 per asset (total number of servers and clients).
The prerequisite is the use of an existing Enginsight instance. Separate provisions apply for the public sector (KRITIS, public sector). If you have any further questions about the SIEM system or other cybersecurity measures, please feel free to contact us at any time.
Yes, we have already automatically connected a large number of firewalls to the SIEM system. If your firewall is not included, we will integrate it within one working week. You also have the option of using our extractors to address individual data sources via regex.
In our documentation >> you will find a detailed infrastructure explanation including. Installation guide and product description for Enginsight SIEM.
We or our experienced partners>> will gladly take care of the installation and setup. Just contact us 🙂
A SIEM system pulls together event data from multiple sources within your network infrastructure, including servers, systems, devices and applications.
By integrating contextual information about users or assets, a SIEM solution provides a holistic overview with additional insights. The collected data is consolidated by the SIEM system and subjected to in-depth analysis to identify deviations from your company’s defined rules of behaviour. In this way, the SIEM system functions as a comprehensive security solution that is based on the thorough evaluation of event data and aims to recognise potential threats. It therefore makes a significant contribution to ensuring the integrity of your network and responding proactively to security risks.
The need for a SIEM system stems from its ability to detect patterns and anomalous behaviour.
Even if a single event does not set off alarm bells, the SIEM tool can detect potential threats by correlating multiple events that would otherwise go unnoticed. The system is designed to perform a comprehensive analysis and trigger notifications as required. These logs are carefully stored by the SIEM tool in a database. This storage enables you to carry out in-depth forensic investigations or prove compliance requirements by having access to detailed records. Thus, a SIEM system not only ensures early detection of potential threats, but also provides the necessary resources for comprehensive security analysis and compliance checks.
A SIEM tool is the software that acts as the central instance for analysis-based cybersecurity within a SIEM system. All event data is recorded in a central location. The SIEM tool assumes full responsibility for analysis and categorisation.Of particular importance here is that the SIEM tool provides the appropriate context that enables security analysts to gain in-depth insights into security events within the infrastructure.
The SIEM is part of the Enginsight Cybersecurity Platform.
Would you like to know how you can improve your IT security with Enginsight? We would be happy to analyze your current status and real needs in the area of IT and network security together with you.




