SECURE THE OPERATION OF YOUR IT ENVIRONMENT IT monitoring software
Recognise anomalies in your capacity utilisation and always be up to date on availability. With the IT monitoring software from Enginsight, you always have an overview of your entire IT environment.
Enginsight is the all-in-one cybersecurity platform from Germany that analyzes your security posture, detects threats and prevents attacks automatically – as SaaS and on-premises.












IT monitoring software All features at a glance
Prevent problems and causes of failures.
Everything in view All availabilities and loadings
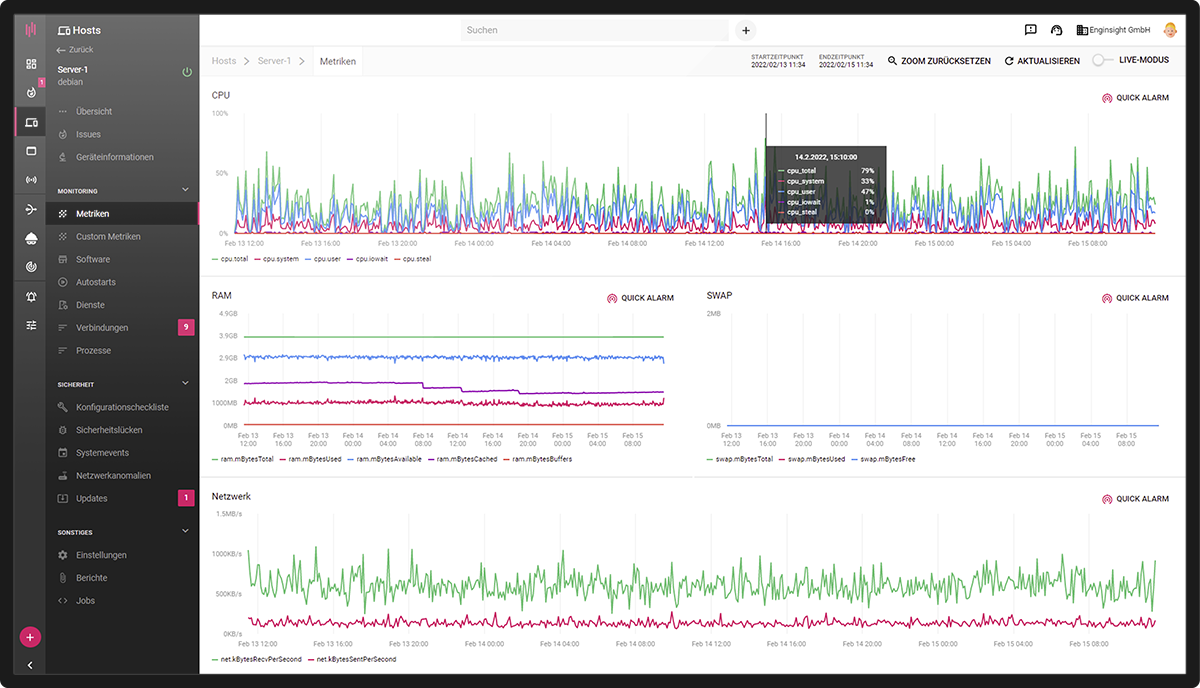
Whether server, client, switch, printer, database or telephone system: Enginsight’s IT monitoring software collects all key figures on the availability and utilisation of your IT for you. This gives you an overview of the status of your entire IT infrastructure in one platform. Server monitoring for Windows and Linux.
- IT Monitoring with and without agent
- Acquisition of individual machine data
- Out-of-the-box metrics, which are directly available to you
- Enrich your monitoring with logs from the SIEM
Continuous safety Ensure compliant operation
Be sure that there are always enough power reserves available, all system-relevant services are running and reachable. In case of deviations and bottlenecks, Enginsight always informs your responsible employee so that he can proactively initiate countermeasures.
- Detect anomalies
- Alert responsible
- Act proactively
AI-based monitoring Intelligent IT monitoring
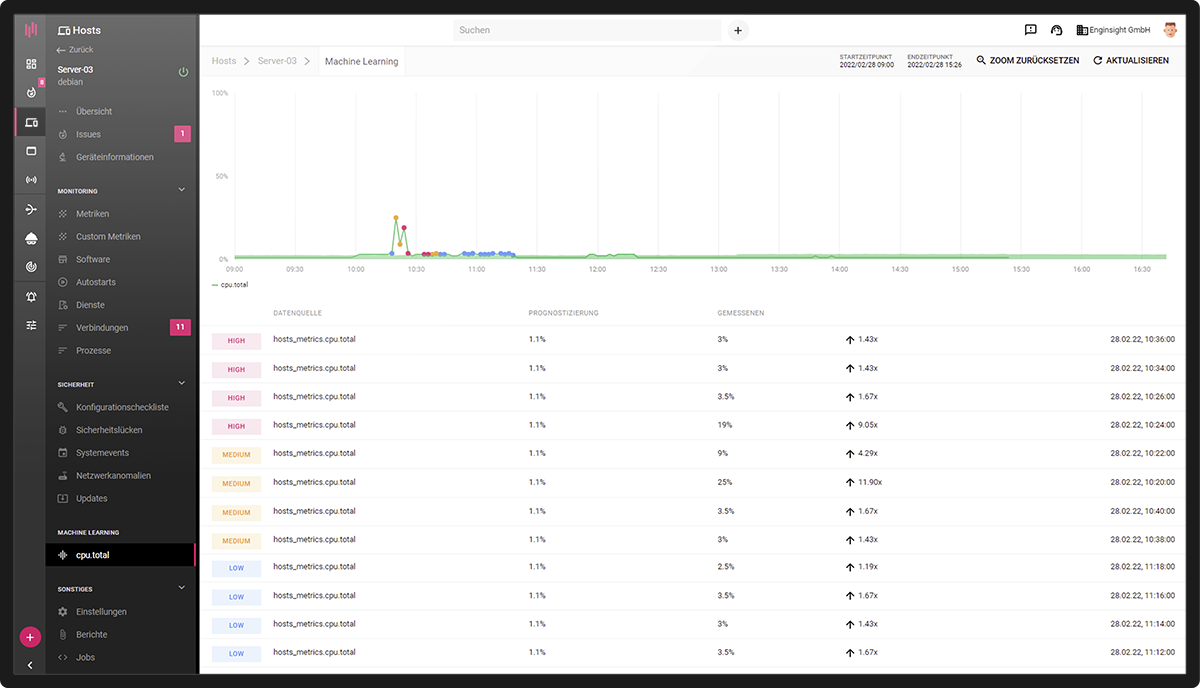
Manually define every limit value? That’s a thing of the past. Thanks to machine learning, Enginsight’s IT monitoring tool understands your metrics, predicts a normal trend and alerts you to anomalies. Increase your efficiency with next-generation IT monitoring.
- Autonomous monitoring
- Based on Machine Learning
- Alerts without fixed thresholds
- More time for administrators with increased security
IT-MONITORING SOFTWARE All system events & more
Maintain control over your entire IT landscape. Thanks to automatisms and machine learning, your IT security will reach a whole new level in the long term. Use IT monitoring as the basis for a holistic security concept.
- Automate your workflows easily thanks to effective vulnerability management.
- Ensure the performance of your web applications reliably and consistently at all times.
- Keep track of all assets in your IT landscape at all times with IT inventory.
functions and solutions Technical details of the IT monitoring software
Would you like to know more about IT monitoring? Then you’ve come to the right place! Find out what Enginsight can do for you automatically in detail when it comes to IT monitoring.
Enginsight enables classic availability monitoring on all servers and clients by installing the Pulsar agent. This includes monitoring CPU, RAM, SWAP, disk and network utilization. In real time, the user receives the metrics in question and can examine them for any problems.
With custom metrics, monitoring can be expanded to include any data that can be displayed over time. This can be, for example, data from a database, backups or sensor data. More specific use cases, such as monitoring a telephone system, are also easy to implement.
- Platform independent: Linux & Windows
- CPU, RAM, SWAP
- Hard disk utilization
- Network load
- Custom Metrics: Databases, backups, sensor data, and more.
The data trajectories of all metrics (standard metrics and custom metrics) can be analyzed and understood by the Machine Learning module to predict the expected normal operation In case of unusual trajectories, it categorizes the deviation as low, medium or high.
Autonomous monitoring of metrics for anomalies allows alarms to be defined without fixed thresholds. This reduces the administrative burden and the number of false positives.
- Monitor all metrics with machine learning
- Detect anomalies
- Alerts without fixed limit values
Enginsight monitors the software on all servers and clients with Pulsar Agent installed. Whether software is installed/uninstalled or whether new autostarts are added thus remains transparent even across large IT environments. Enginsight also includes monitoring of whether all system-relevant services and processes are running. Particularly relevant from a security perspective: If an application on a server opens a new port, Enginsight triggers an alarm – if desired.
- Monitor installations and uninstallations
- Services and processes monitoring
- Port monitoring
Enginsight examines the log files of all servers and clients with installed Pulsar agent for security-relevant events, intersects them and evaluates them. Successful and failed login attempts can be monitored, as well as the creation of new users or when new administration rights are assigned. Monitoring of access to sensitive files and directories can also be integrated into Enginsight’s system log monitoring.
- Login attempts
- New users and rights
- Access to sensitive directories
Network devices on which no agent can be installed can also be monitored with the IT monitoring software from Enginsight. Simple health checks check the availability of devices and ports in the network. Monitoring via SNMP enables the monitoring and analysis of more data, for example the network utilisation of a router interface or the error status of a printer.
Thanks to the many integrated Management Information Bases (MIBs), setting up SNMP monitoring is greatly simplified. If no suitable MIB is available, users can upload their own MIBs. As the user then defines expected values, deviations are quickly recognised and alarms are quickly activated.
- Ping/Port-Monitoring
- SNMP-Monitoring
- large pre-selection of MIBs
- Upload own MIBs
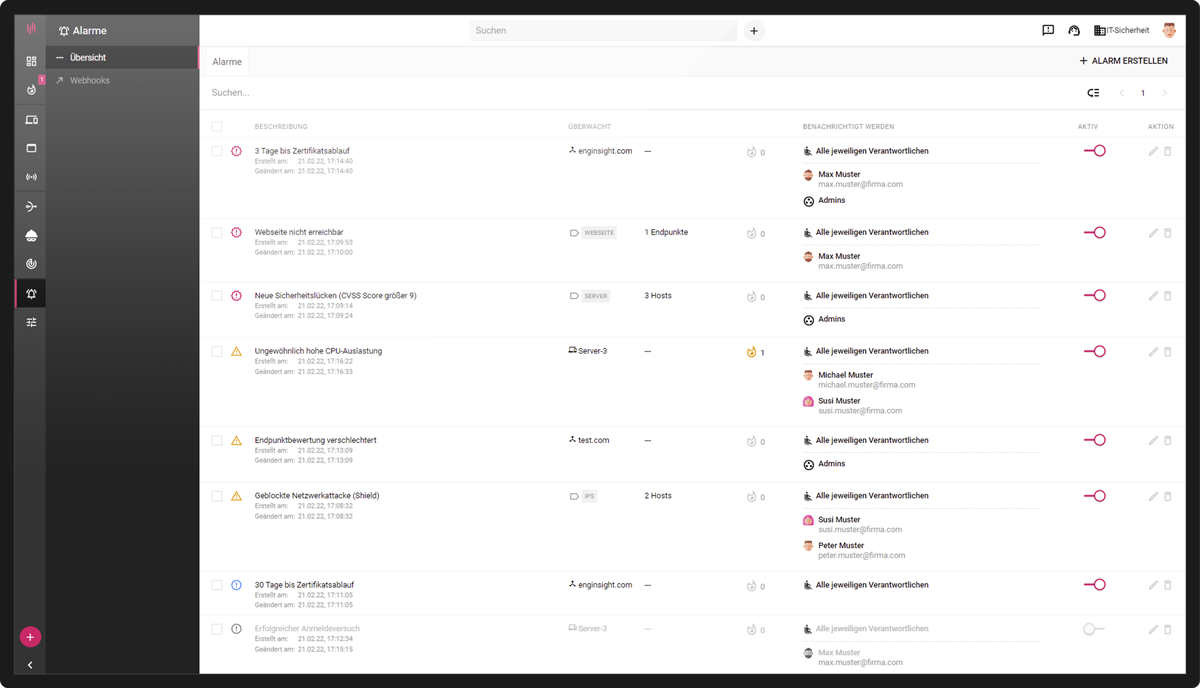
All data aggregated by Enginsight’s IT monitoring flow together in the Enginsight platform and are clearly displayed. With alarms, responsible persons can be informed in a targeted manner about safety-relevant incidents or deviations. A tag system for grouping all assets facilitates the management of alarms.
- Collected results in the Enginsight platform
- Define and alert responsible persons
- Alert via email, SMS, Slack, Mattermost, Microsoft Teams
- Tags to manage efficiently
Reference video
IT’S NOT ABOUT IT SECURITY, IT’S ABOUT OPERABILITY AND RESILIENCE
Effective risk management requires continuous condition monitoring in combination with preventive measures as well as a data basis for forensic analyses.

FAQ on IT monitoring and failover
IT monitoring is a process in which various aspects of a company’s IT landscape are monitored using monitoring software and corresponding analyses. Any problems identified are recognised more quickly and can be solved efficiently with appropriate instructions.
Companies can benefit from IT monitoring software in many ways:
Ensuring system availability: An IT monitoring tool is crucial to ensure the availability of your business-critical applications and services. It consistently monitors all components of the IT landscape and alerts your IT team in the event of deviations.
Increased performance: IT monitoring software and the continuous monitoring of your IT systems that it provides enable you to optimise resources and maximise efficiency.
Cybersecurity: IT monitoring software detects suspicious activity and security breaches at an early stage, allowing companies to act proactively to minimise security risks.
Faster response and reduced downtime: The holistic solution of IT monitoring software replaces manual monitoring of your IT landscape and ensures significantly fewer system failures. IT managers can recognise problems more quickly and take appropriate steps to rectify the diagnosis.
IT monitoring software is a technology that continuously monitors the performance and security of an organisation’s IT systems and networks. The IT monitoring tool enables organisations to monitor their digital infrastructure in real time and ensure that everything is running smoothly.
Monitoring gives you a detailed insight into all aspects of your IT infrastructure, from servers and networks to applications and databases. The IT monitoring tool collects data, analyses it and presents it in an understandable form so that IT teams can gain immediate insights and act quickly when problems occur.
The daily look into the monitoring tool is important. How about being immediately informed about your security status when you take this look?
Work on your daily tasks alone or together as a team using the Enginsight platform.
Often, when using Enginsight, existing tools can be replaced, license costs can be saved, or efficiency can be improved.
Enginsight IT monitoring is part of the Enginsight Cybersecurity Platform.
Would you like to know how you can improve your IT security with Enginsight? We would be happy to analyze your current status and real needs in the area of IT and network security together with you.