IT-ASSET MANAGEMENT SOLUTION (ITAM) IT inventory
Keep track of all IT assets on your network at all times.
Automated inventory including vulnerability detection in one platform.
Enginsight is the all-in-one cybersecurity platform from Germany that analyzes your security posture, detects threats and prevents attacks automatically – as SaaS and on-premises.












Automatic detection and unlimited IP inventory IT asset inventory made easy
Through permanent monitoring, you have an overview of all relevant information of your IT landscape at all times.
Assetmanagement Inventory of all assets in the network
Whether switch, printer, client or server – all devices with an IP address can be inventoried completely automatically with Enginsight. This effectively prevents IT systems from flying under the radar.
- Permanent monitoring of network traffic
- Audit-proof asset inventory
- Ideal basis for security audits
- Live detection of new devices in the network
Monitoring with insight Device information
Retrieve in-depth information about all servers and clients by installing an agent on them. This way you enrich your inventory with valuable information and take it to the next level.
- Retrieve device information
- Carry out safety analyses
- Central IT monitoring software
- Software Inventory
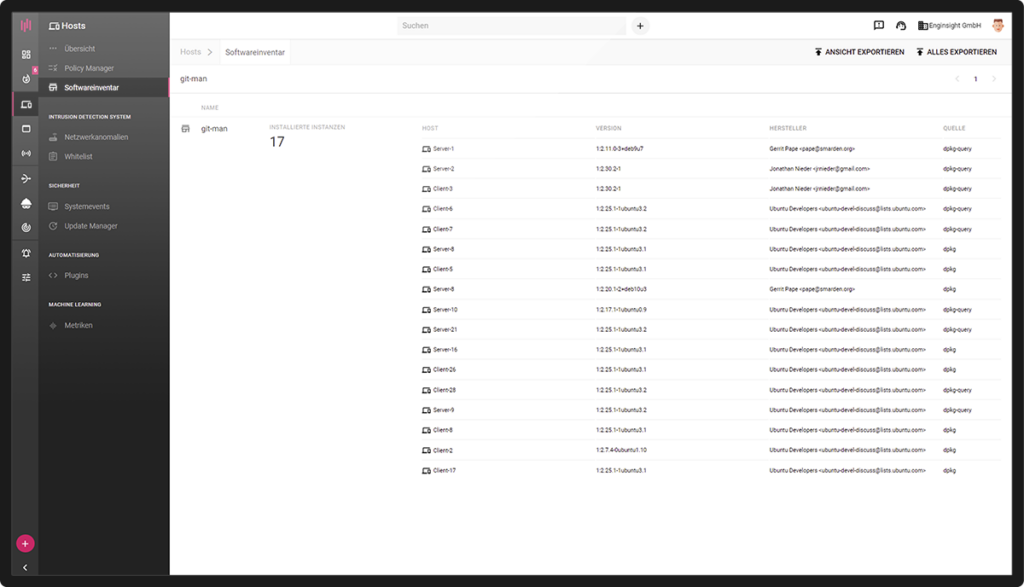
Automation & Workflows Automate software inventory
Automate your software inventory and get an overview of which software is installed on which servers and clients. Search the inventory for specific software and set an alert on new and remote installations.
- Search entire IT infrastructure for software
- Export software lists
- Detect outdated versions
- Classification of all network devices
IT Asset Management Solution (ITAM) Technical details
Would you like to know a little more? Then you are exactly right here! Find out what Enginsight does for you in detail when it comes to IT inventory in a completely automated way.
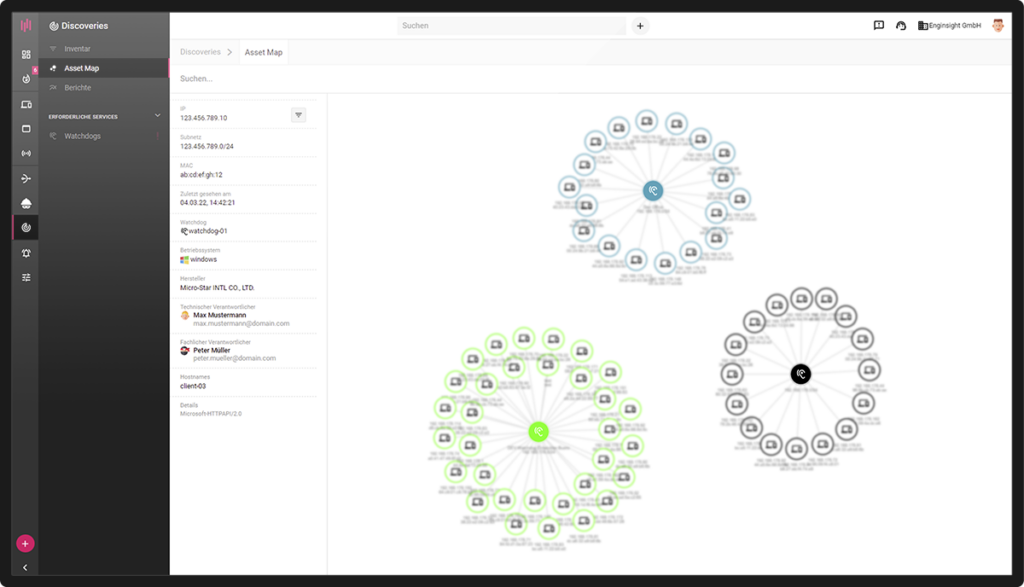
The installation of the Watchdog software component in the network enables permanent monitoring of the network traffic according to its participants. With regular active network scans, the Watchdog also provokes network connections and thus finds IP addresses that have not generated any network traffic on their own.
Automatically, Enginsight attempts to categorize the detected assets. In addition, the user is free to enter further data on the asset for documentation purposes (e.g. description, location, responsibility). The assets can also be grouped via tags. To establish the distinction between official and potential shadow IT, assets can be marked as appraised. To use the data externally, the lists can be exported.
- Scan network fully automated
- Interactive Asset Map
- Complete network inventory
Further information: How do I create an effective IT inventory of my assets?
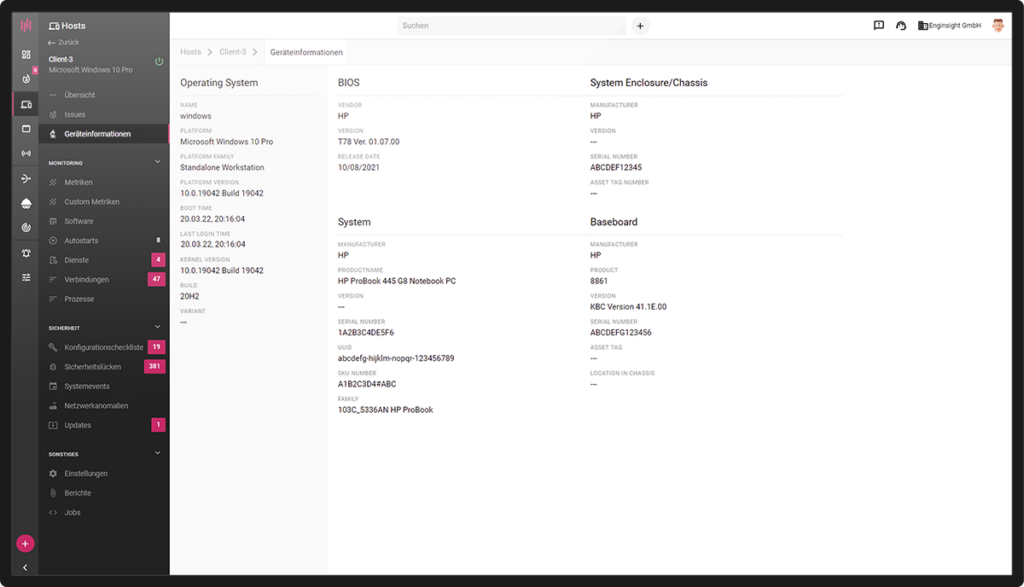
The installation of the Pulsar agent on servers and clients realizes an agent-based inventory. Thus, assets outside the network can also be included in the inventory. In addition, the inventory via the agent allows more information to be retrieved automatically.
System information provided by the mainboard is available as device information, such as model designations and serial numbers. Here, too, the data can be expanded (e.g. description, location, responsibility) and the assets can be grouped via tags. Also included is a software inventory with a total overview of all software. This opens the possibility to search all servers and clients specifically for software with a search command or to export lists with installed software.
- Platform independent: Linux & Windows
- Inventory also outside the network
- Retrieve detailed data automatically
- Software inventory included
Team members can be defined as responsible persons for each asset. On the one hand, the responsibilities fulfill important documentation requirements, and on the other hand, they form the basis of Enginsight’s alert system. In the event of safety-relevant incidents or deviations from normal operation, the right people are always informed.
- Define responsibilities for all assets
- Fulfill documentation requirements
- Assign alert to responsible persons
The inventory is the ideal basis for a security audit of the entire IT infrastructure. Therefore, the IP addresses detected via the network-based asset inventory can be selected as target systems for the automated penetration test. Servers and clients inventoried with Agent are automatically monitored for security issues. For example, the software inventory provides the basis for a scan for software with security vulnerabilities (CVE check).
- Use asset inventory for automated pentesting
- Security monitoring of server and clients
- CVE scan

FAQ about IT inventory
The inventory of the company’s own IT brings many advantages and facilitates the daily administration routine. It helps to…
- to improve IT asset management.
The inventory of IT represents the first step of an IT asset management (ITAM). The goal of ITAM is to reduce costs and risks while increasing productivity. - Combating shadow IT.
In addition to the official IT infrastructure introduced by the IT department, companies often use IT systems that run under the radar. They are introduced by employees or departments without the knowledge of IT. Shadow IT is on the rise and entails a rat’s tail of problems. A well-implemented IT inventory prevents the emergence of shadow IT. - Increase IT security
What has not been systematically recorded is difficult to control. An overview of the existing IT systems therefore also helps to increase the security of the IT landscape. - prepare an IT audit.
An inventory of the entire IT infrastructure is the perfect prerequisite for a comprehensive security audit. In the audit, all information technology systems are subjected to a risk and vulnerability analysis. - Enable certifications
An IT inventory is a requirement of many certifications (e.g. ISO 27001). Certifications increase the trustworthiness of companies and are often a requirement for the establishment of business relationships.
Hybrid processes are recommended in order to utilize the advantages of agentless and agent-based processes and to compensate for disadvantages. Here, network-based inventory is supplemented by agent installation on important assets or assets located outside the network.
On the one hand, network-based IP inventory ensures that no assets go undetected and provides availability monitoring. On the other hand, agents installed on assets enable more information to be captured automatically and include assets located outside the network.
All Agentless inventory, persistent monitoring of your network for new devices, and ping, port, SNMP monitoring is available to every Enginsight customer at no charge.
Enginsight’s IT inventory and asset management is part of the Enginsight Cybersecurity Platform.
Would you like to know how you can improve your IT security with Enginsight? We would be happy to analyze your current status and real needs in the area of IT and network security together with you.