Your effective IT security workflow
No more dozens of individual tools! Enginsight brings together the most important tools so that you can manage your IT security easily, quickly and conveniently – by making the invisible visible and the unsafe safe.





QSil AG, quartz glass manufacturer
The Enginsight features at a glance
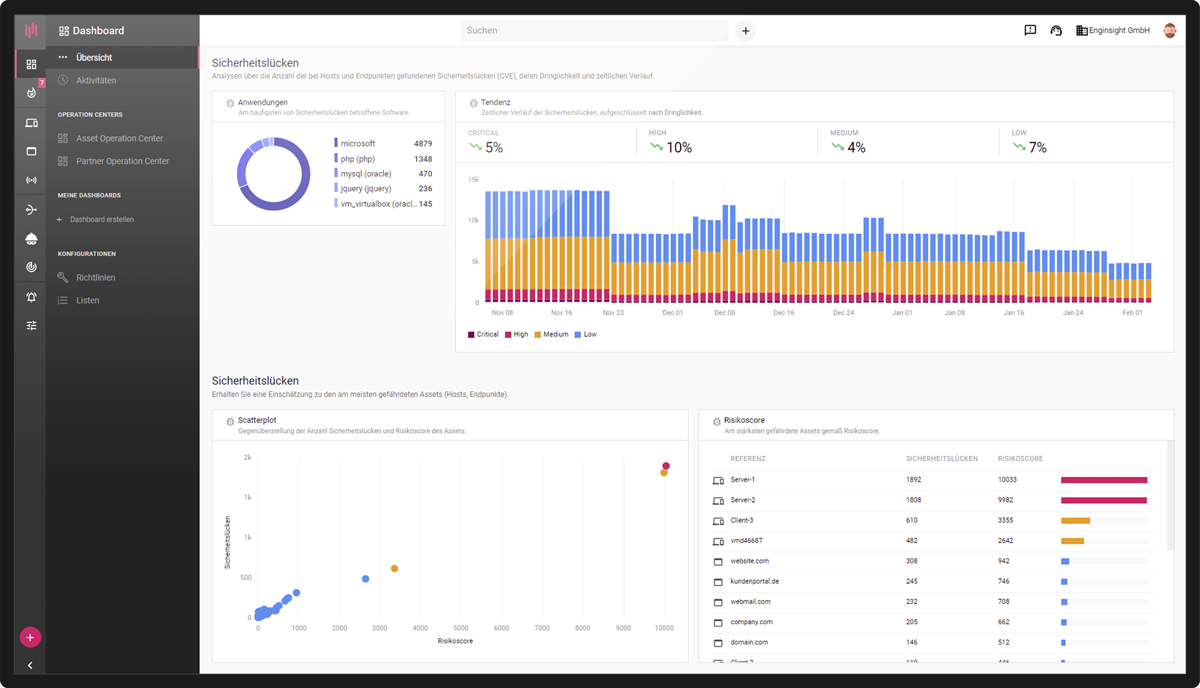
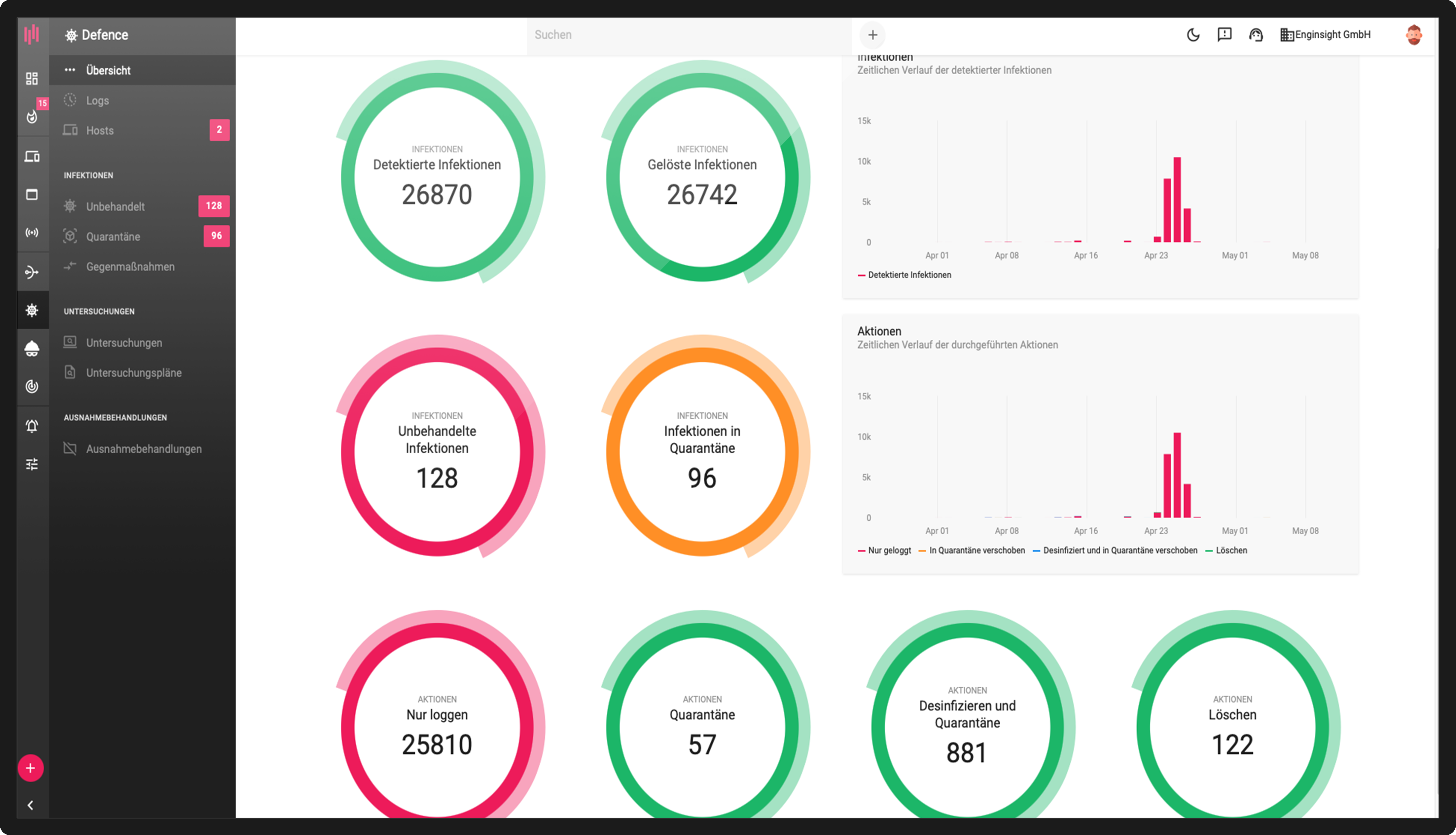
Vulnerability management
Gain valid insights into potential security vulnerabilities and eliminate them before someone else can exploit them. With Enginsight, you know exactly what’s most important to you now.
- Correct prioritization thanks to the view of the entire IT
- System zur Angriffserkennung gem. BSI
- Highest quality of data
- Proactively eliminate hazards
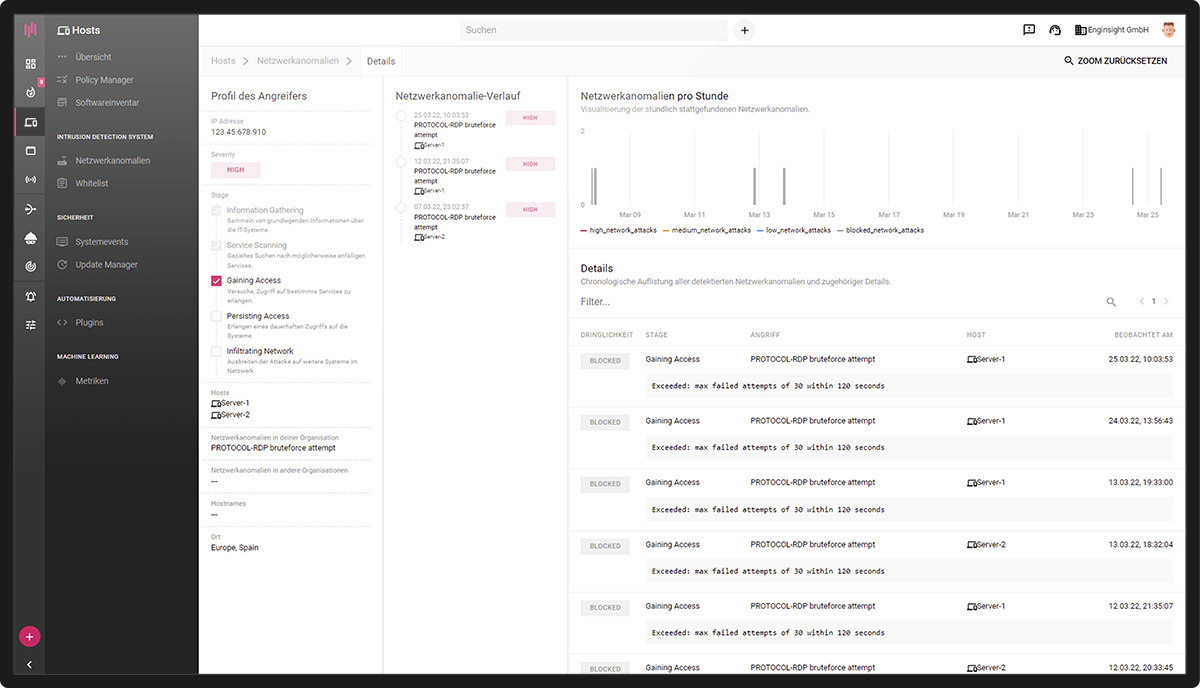
Intrusion Detection and Prevention
With an intrusion detection system, you scan network traffic for attacks – the intrusion prevention system then blocks them. In combination, they make the invisible visible – and the insecure secure.
- Analysis and evaluation of the attacks
- Flexibility: Scalable and home office ready
- View into internal network
- Microsegmentation
Automated penetration tests
View your IT infrastructure from an attacker’s perspective and uncover potential vulnerabilities. Check your IT from the inside and outside.
- Automatable pentests
- Clear audit reports
- Concrete recommendations for action
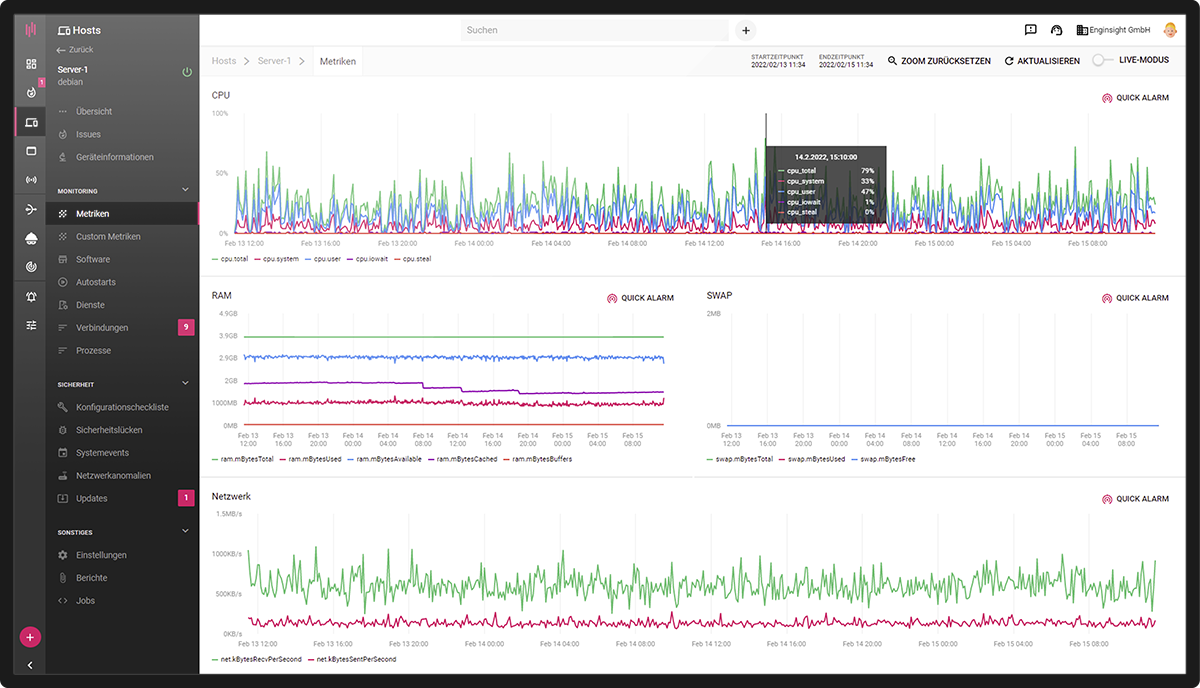
IT Monitoring
Reliability is the be-all and end-all of your IT security strategy. Stay in control at all times and set the foundation for secure IT! Server, Clients, alles Assets zentral verwalten.
- All availabilities and loadings
- Ensure compliant operation
- IT-Management Software
- Intelligent monitoring with machine learning
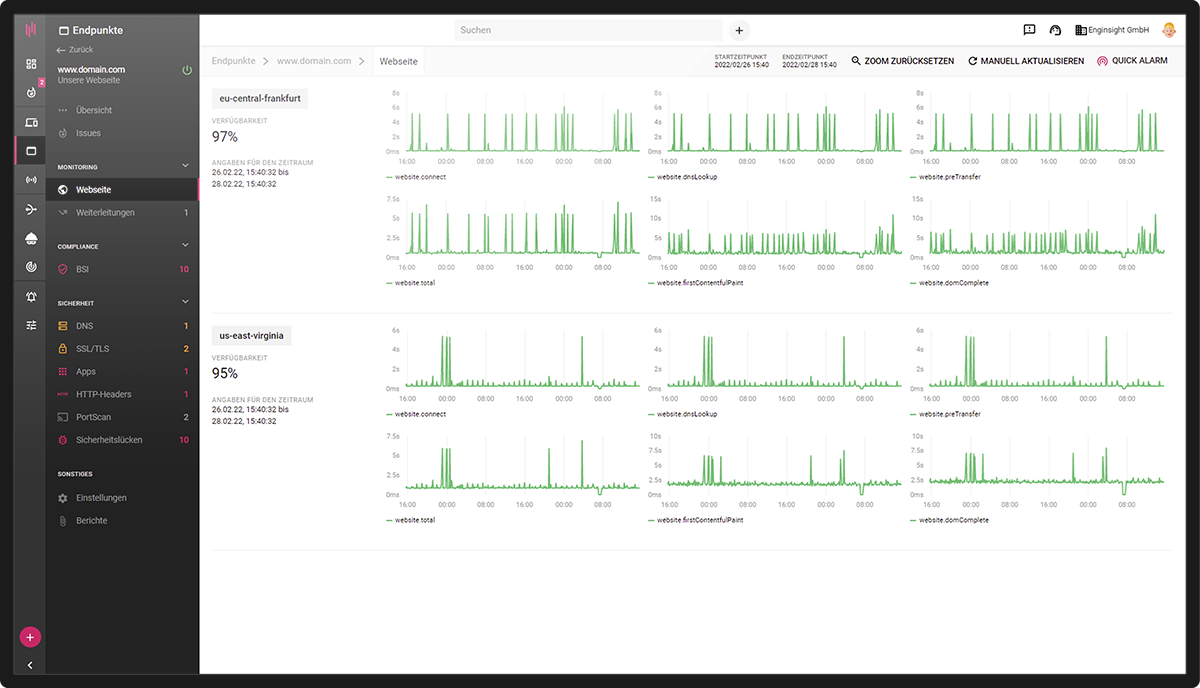
Website monitoring
Your website should always be 100% accessible and 100% secure. Address vulnerabilities and stay up to date on utilization and availability.
- Performance and availability
- Determine security level
- Monitor encryption
Endpoint Detection and Response
Detect viruses and malware before it can do any damage. At the same time, you always have a full overview of what is happening on the servers and clients.
- Advanced anti-virus scan
- All-round protection against malware
- Centralized management
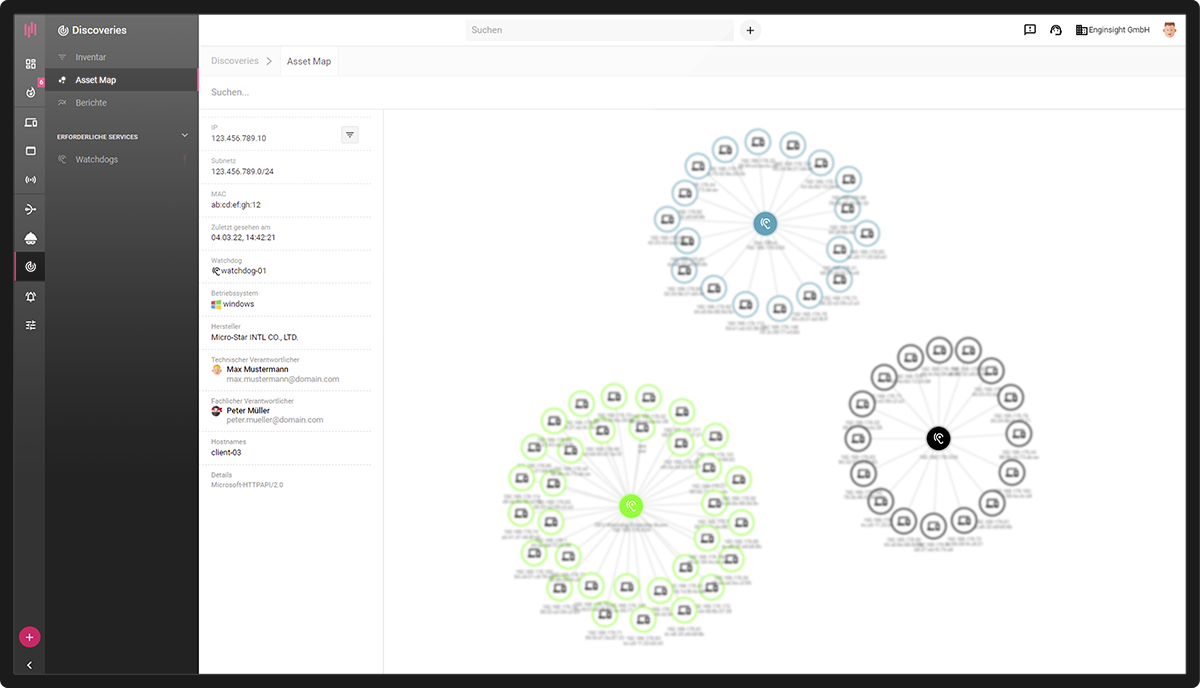
IT Inventory
Through permanent monitoring, you have an overview of all relevant information of your IT landscape at all times.
- Inventory of all assets in the network
- In-depth data thanks to agent
- Automate software inventory
With Enginsight you are always one step ahead
Only those who know their IT are able to react quickly and eliminate vulnerabilities before they can be exploited. Monitor and manage your IT infrastructure from one interface with Enginsight. This relieves your IT department and increases the security of the corporate network.

Always keep an eye on your IT environment, regardless of time and place. Work more effectively by centrally viewing all relevant information and enabling consistent monitoring of your IT landscape.

Make the security status of your IT transparent and act proactively before vulnerabilities become a problem. Save time every day – with automated workflows.
Keep your focusand know at any time which work really needs your attention– through valid knowledge of your construction sites in IT security.
Scan your IT for potential vulnerabilities now and pentest your IT - all included in the 14-day trial.