Host based intrusion Detection and Prevention Your attack detection system on any server and client
What to do if the attacker got behind the firewall or there are no patches available for vulnerabilities? No problem. Now your Intrusion Detection and Prevention System from Enginsight takes care of that.
With Enginsight, you can detect attacks and anomalies on any client and server and block them automatically.
Perfect for hybrid IT environments: Cloud, Local, Home Office
This is why you need an IDS Dig out rat nests!
Mark Semmler (born 1973) has been working worldwide for more than 25 years to secure information and IT infrastructures. Here he explains why an intrusion detection system is important and what it does in the first place. Also understandable for non-techies 😉











How the IDS/IPS - Intrusion Detection and Prevention System works Detect and block attacks
With the Intrusion Detection System, you scan network traffic for attacks – the Intrusion Prevention System then blocks them. In combination, they make the invisible visible – and the insecure secure.
LIVE DETECTION OF CYBER ATTACKS
Analysis and evaluation of the attacks
Enginsight’s Intrusion Detection and Prevention System keeps you up to date on the status of potential attacks. Learn where attacks originate and how far they have come. Your complete internal network monitoring in one platform.
- An overview of all attacks in the IT environment
- Analysis and evaluation of the attacks
- Inform responsible persons automatically
- Automatic response / Bocking
Network security on any device
Scalable and home office ready
Home office devices in particular are usually more vulnerable to attacks. With Enginsight you stay secure and benefit from hardware-independent flexibility and scalability
- Enginsight grows with your IT - without hardware upgrades
- Best security even outside the company network
- Performance and availability in harmony
Proactive – Detection & Response
View into internal network
The decentralized approach allows you to detect and block attacks not only from the outside, but also in the internal network. Even with successful infiltration, attackers cannot spread further.
- Lateral Movement Detection of the attack
- Isolation of infected systems protects against outages
- Protects you where a firewall reaches its limits
Making the invisible visible
Detect cyberattacks in your network at an early stage
A host-based intrusion detection and prevention system (HIDS/HIPS) offers several advantages.
First, it enables close monitoring and analysis of system behavior and traffic directly on the host to detect anomalies and potential threats.
Second, it provides a specific layer of protection against targeted attacks on individual systems and can operate without being connected to a network.
Third, it enables direct response to detected threats, for example, by blocking or quarantining malicious processes.
Play IDS/IPS video
Functional scope Intrusion Detection and Intrusion Prevention System Technical details of the IDS/IPS
What makes an attack detection system technical?
Below you will find the technical details of the Intrusion Detection and Prevention System with Enginsight and why automation plays a very important role in it.
The technical basis of Enginsight’s intrusion detection and prevention system is formed by the Pulsar agents installed on all servers and clients; the IDS/IPS is therefore host-based. This is where Enginsight differs from network-based systems where the sensor is integrated at the switch, behind the firewall or in the firewall. This means that the IDS/IPS can be scaled hardware-independently for any size of company and remains active even if a client leaves the company network, e.g. to the home office.
The decentralized approach also makes it possible to detect and block attacks from within the internal network or even within a network segment. Attempts by hackers to spread further in the network after successful infiltration can thus be effectively prevented.
- Host-based
- Scalable
- Homeoffice-ready
- Detect and block attacks from internal network
Further information about the Intrusion Prevention System (IPS) for companies
Enginsight examines the content of network traffic for a variety of suspicious activities. By targeting very basic attack types, the IDS covers all major categories of network-based attacks. This already makes it almost impossible for the attacker to spy out information, gain access or spread further into the systems unnoticed.
- Port Scan (TCP, UDP)
- Spoofing (ARP, DNS)
- Bruteforce (e.g. on SSH, FTP, RDP, HTTP)
- Cross Site Scripting
- SQL Injection
- … and much more!
The scope of attacks that Enginsight detects and blocks can be extended to include those described in the SNORT Communiy Rules. Thus, the IDS/IPS also covers more specific attacks, for example on certain applications. For example, attacks on Microsoft IIS or Exchange Server, attempts to access sensitive data on a web server or CGI attacks can be identified. With just one click, SNORT Community Rules can be activated to benefit from advanced detection capabilities.
- Detect and block attacks on specific software
- benefit from the large scope of SNORT Community Rules
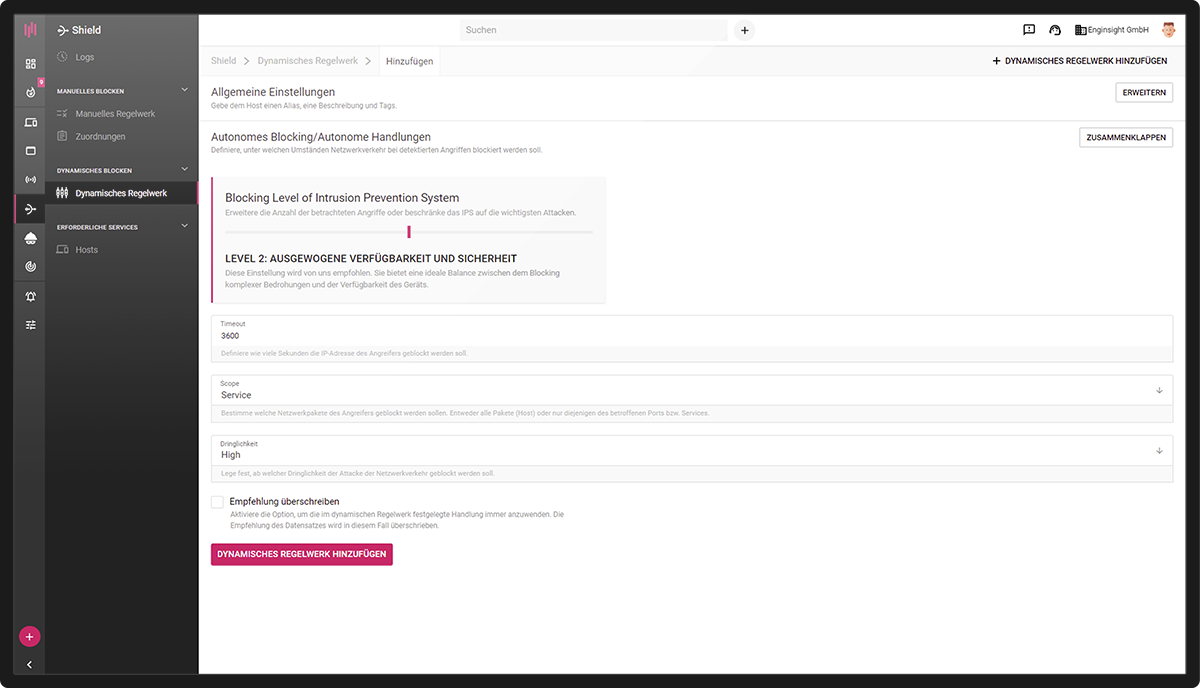
Detection and blocking levels can be assigned to all servers and clients according to their protection needs. This brings security, performance and availability into the ideal balance. By grouping servers and clients beforehand using the tag system, the user can then set the desired levels for the groups using a simple slider.
- Easy configuration
- Take over risk assessments
- Align security, performance and availability
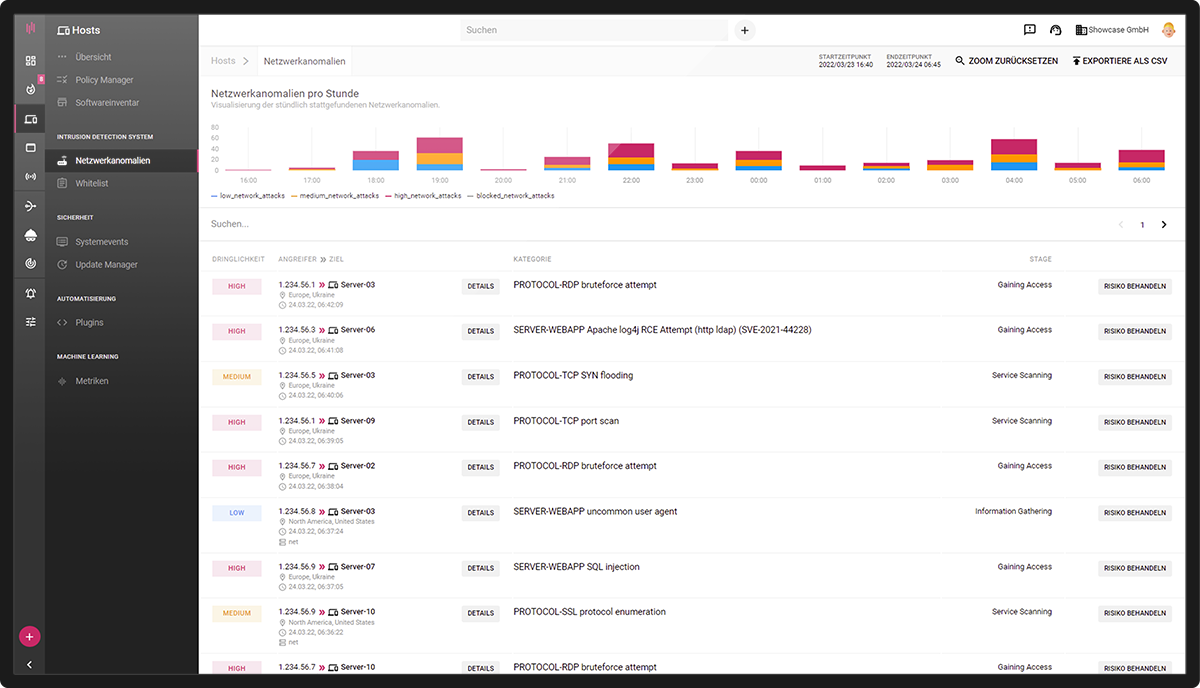
In the platform, Enginsight consolidates the network attacks detected on all servers and clients. IP addresses, origin and attack vectors used can be viewed here. Each attack is rated according to urgency (high, medium, low).
In addition, Enginsight analyzes the stage the attacker has already reached: from information gathering, to trying to gain access, to spreading to other systems in the network. Responsible persons can be informed about critical conditions with an alert.
- An overview of all attacks in the IT environment
- Analysis and evaluation of the attacks
- Inform responsible persons automatically
Customized whitelist entries can be used to define unusual but harmless behavior to ensure availability and smooth operation. For example, a whitelist entry is the right choice to allow the software component of Enginsight’s penetration testing to work properly. But other harmless activities on the network can also be handled specifically by IP address, attack vector, protocol and software.

FAQ on Intrusion Detection and Prevention
-
Protection against internal threats: Because HIDS is installed directly on the host, it can detect and respond to internal threats and insider abuse, while Firewall-IDS is primarily focused on external threats.
-
Granular monitoring and control: HIDS enables more granular monitoring and control of individual systems and applications and can take specific host-level defensive actions.
-
Network structure independence: HIDS is less dependent on the network structure and can also be used in environments where network traffic is not centrally routed through a firewall.
-
Anomaly and behavior change detection: By monitoring system activity and logs, HIDS can detect behavioral changes and anomalies at the host level that may be missed by a firewall IDS.
-
Offline and standalone protection: HIDS can also protect systems that are not constantly connected to the network or operate standalone, as it does not depend on a network connection.
Enginsight’s Intrusion Detection and Prevention System is part of the Enginsight Cybersecurity Platform.
Would you like to know how you can improve your IT security with Enginsight? We would be happy to analyze your current status and real needs in the area of IT and network security together with you.