Cybersecurity Risk analysis
Want to make sure your business is protected against cyberattacks? A security audit is the first step. Our team of experts will thoroughly assess your security measures and identify critical vulnerabilities that leave your organization vulnerable.
With our recommendations, you can protect yourself and your company’s sensitive information and assets – invest in a security audit today.










Why do I need a security audit?
A security audit is a systematic assessment of the security of an organization’s information systems and processes. The purpose of a security audit is to identify vulnerabilities in the system and recommend actions to address those issues and improve the overall security of the system.
IT security audits are an important part of maintaining the confidentiality, integrity and availability of an organization’s information and systems.
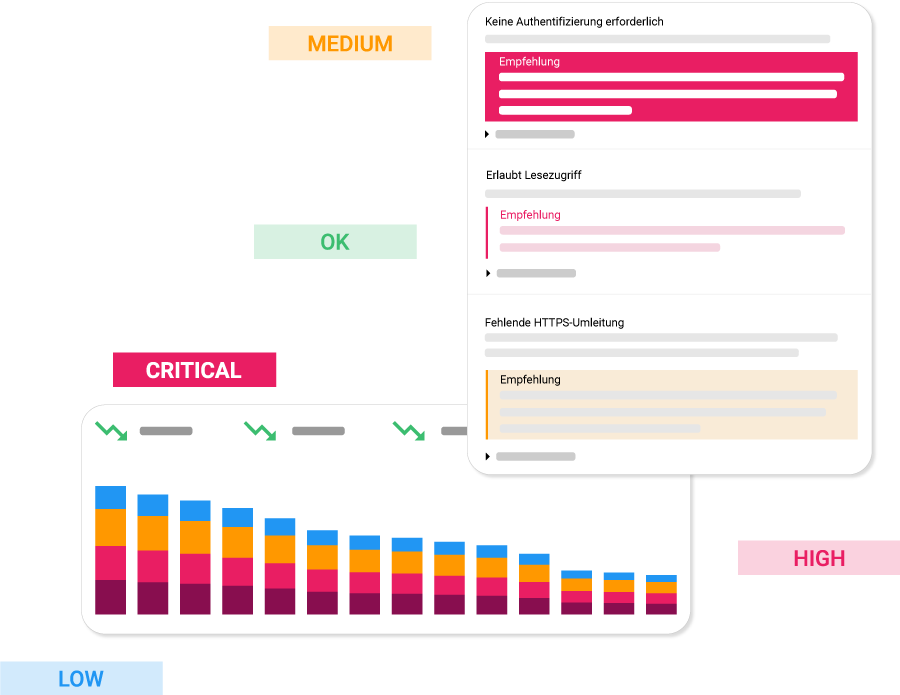
Can you measure your IT security and really know what's going on? Create the transparency you need through the lens of a hacker. This allows you to immediately identify the neuralgic points of your IT.
Meet the regulatory requirements of a wide range of standards, e.g. ISO 27001, TISAX, B3S, BAIT, VAIT, with an Enginsight security audit or penetration test, etc.
The objective view of the pentest gives you insight into whether your current attack detection measures are working, beyond the report of your security vulnerabilities.
Obsolete ISDN converter for intercom and door, which had access to the Internet.
Routing 100+ VLANs through the router and open NAS systems with research data.
User passwords stored in AD notes and printer with domain admin rights
System control no longer AirGap secured and accessible from outside due to connected headset
Main building surveillance camera established an open S2S VPN to the security company
After an administrator left, the firewall was completely disabled and ignored all data flow via any any rule.
What happens during a security audit?
Only those who have everything in view can really assess their own risk and make concrete
take measures. With the help of the Enginsight platform in combination with many years of security / pentest know-how, we analyze the security status of your IT, show you all the security gaps that have been uncovered in a meaningful report and discuss further recommendations for action with you.

- (Hidden) Data Discovery & Information Leakage
-
- Finding potential public and hidden information channels
- Startpoint of Lateral Movement
- Information Gathering and Vulnerability Identification
- Sensitive Information Breach (Where can internal data leak)
- Detection of non-publicly visible files e.g. DB dumb, password files, password dumb in root folder, which was downloadable
The information gathered about the system (Information Gathering) will be used to tailor Enginsight to your system to execute the appropriate attack vectors and immensely reduce the false positive rate to expose vulnerabilities.
- Vulnerabilities from 3 perspectives
-
During the security audit, we validate the vulnerabilities and potential entry points from three angles:
- Black-Box– analysis from the outside on your web applications (web security analysis)
- Grey-Box-analysis from the outside through the glasses of an attacker (authenticated or non-authenticated). Targets are everything that has an IP address, e.g. servers, clients, websites, Fritzbox, Active Directory, IoT devices, etc.
- White-Box-analysis directly on your Windows or Linux server and clients incl. directly possible countermeasures (patching and mitigation / CWE).
- Insider Attacks on your Infrastructure
-
- Finding incorrect configurations that lead to potential vulnerabilities
- Highlight vulnerable points where an attacker can take control of your systems
- Gathering critical information that is exploited by attackers
- Verification of the trustworthiness of your communication / protection against identity theft
- Active Directory scanning to see if important company information can be found without Auth
- Intrusion Detection
-
Detect anomalies, attacks or existing hackers through Enginsight’s host-based intrusion detection system, right live on your endpoint.
Protection against unknown threats: A HIDS uses rules or signature patterns to identify threats that are known, but also the ability to detect anomalies that may indicate possible threats.
Insider threat detection: A HIDS can help detect insider threats by monitoring user and process activity on the system and detecting anomalies that may indicate potential threats.
Complementing network security tools: A HIDS can be used to complement network security tools such as firewalls and network intrusion detection systems (NIDS) to provide a comprehensive security solution.
- Finding potential public and hidden information channels
- Startpoint of Lateral Movement
- Information Gathering and Vulnerability Identification
- Sensitive Information Breach (Where can internal data leak)
- Detection of non-publicly visible files e.g. DB dumb, password files, password dumb in root folder, which was downloadable
The information gathered about the system (Information Gathering) will be used to tailor Enginsight to your system to execute the appropriate attack vectors and immensely reduce the false positive rate to expose vulnerabilities.
During the security audit, we validate the vulnerabilities and potential entry points from three angles:
- Black-Box– analysis from the outside on your web applications (web security analysis)
- Grey-Box-analysis from the outside through the glasses of an attacker (authenticated or non-authenticated). Targets are everything that has an IP address, e.g. servers, clients, websites, Fritzbox, Active Directory, IoT devices, etc.
- White-Box-analysis directly on your Windows or Linux server and clients incl. directly possible countermeasures (patching and mitigation / CWE).
- Finding incorrect configurations that lead to potential vulnerabilities
- Highlight vulnerable points where an attacker can take control of your systems
- Gathering critical information that is exploited by attackers
- Verification of the trustworthiness of your communication / protection against identity theft
- Active Directory scanning to see if important company information can be found without Auth
Detect anomalies, attacks or existing hackers through Enginsight’s host-based intrusion detection system, right live on your endpoint.
Protection against unknown threats: A HIDS uses rules or signature patterns to identify threats that are known, but also the ability to detect anomalies that may indicate possible threats.
Insider threat detection: A HIDS can help detect insider threats by monitoring user and process activity on the system and detecting anomalies that may indicate potential threats.
Complementing network security tools: A HIDS can be used to complement network security tools such as firewalls and network intrusion detection systems (NIDS) to provide a comprehensive security solution.
What do I have to do, to protect my IT?
As part of the IT security audit, we analyze your IT environment together with you and advise you on the points that are important to you.
We provide you with the Enginsight application environment in your data center (or alternatively as SaaS) and place the necessary software sensors.
We actively involve you and concretize first quick wins to increase your security level.
We evaluate and interpret the vulnerabilities and incidents we find and, in the best case scenario, resolve them directly with your IT.
In this way, we enable you to ensure an optimal level of security for your services and systems
and thus effectively protect yourself from damage caused by cybercrime.

Initial analysis of your current security status in a personal preliminary meeting with one of our security experts and definition of the test set.
Setting up Enginsight software in your IT environment.
-
Surface and depth scans
-
Vulnerability scan
-
Intrusion Detection
-
Attack simulation
-
Actual state analysis
Recommend actions & debrief to derive actions and plan optimization points.
Your Audit request offer
- Automated pentest
- Automated vulnerability analysis
- Asset inventory as a basis for penetration testing
- Information gathering from a hacker's point of view
- Password check with brute force
- Specific attacks on detected services
- Web-based attacks
- Network vulnerability scan (CVE scan)
- Extend attacks through custom scripts
- Clear risk assessment
- Concrete recommendations for action
Security Audit FAQ
Enginsight’s classic security audit covers a maximum of 4 x 24 networks and can be carried out in one working day. For larger environments, we discuss the effort estimate with you individually. If you have specific requirements for the penetration test, this may also affect the runtime.
The classic Enginsight Security Audit for max. 4 x 24 nets costs approx. 5.000,- Euro. After a first preliminary discussion you will receive an individual offer.
The security audit / penetration test is performed by security experts of Enginsight GmbH or by qualified partners (IT service providers).
Normally not, as we have developed a gentler method than burdening your systems with highly invasive exploits. Failure could occur in the following cases: The target/machine is already running at 99% load and/or is so poorly configured that any PING will cause the device to fail. However, this would also be a good finding in the context of penetration testing.
Everything that can be reached via an IP. This includes in general: server, client, websites, Fritzboxes, databases, web applications, Active Directory and many more.
If we encounter something “new” at your site, we can also offer possible tests here after consulting with you.
Our security audit provides you with clear and actionable recommendations for action and status analyses, enabling informed decisions to be made at management level as well.
You can then decide whether you want to/can implement the recommendations directly yourself or have an Enginsight partner do it for you.
Enginsight Security Audits can be performed by you or an Enginsight partner on a regular basis after customized training. It is most useful to do a check every time something has been changed in your IT.
If you use Enginsight as a permanent security software, the system automatically performs security checks in the background and alerts you in case of an attack or prevents it proactively.


