Automated Penetration Tests
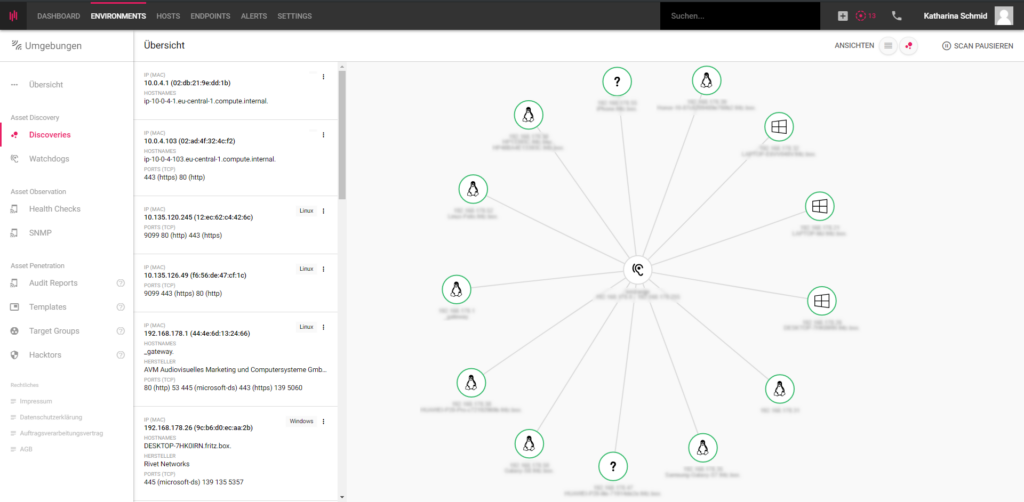
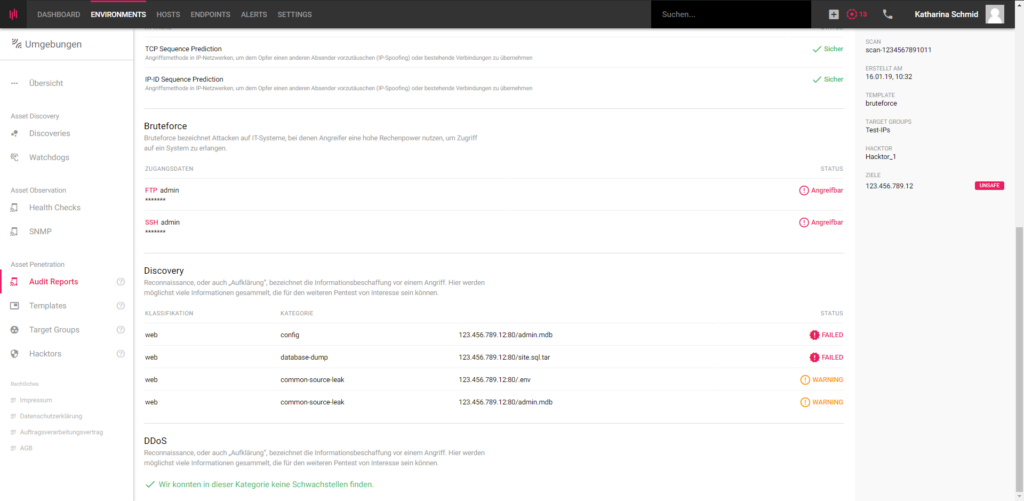
Enginsight offers a comprehensive set of features for analyzing and securing your system landscape. This includes the possibility to set up automated pentests and to repeat them according to defined templates.
You will receive comparable audit reports.